When we speak of cryptography, particularly in the realm of private keys, it is akin to discussing the intricate lock mechanisms used to secure a treasure chest. The private key serves as the exclusive key to this lock, safeguarding sensitive information from the prying eyes of malfeasants. However, the robustness of this security paradigm rests not solely on the strength of the key itself but also on the strategies employed by those intent on breaching such fortifications.
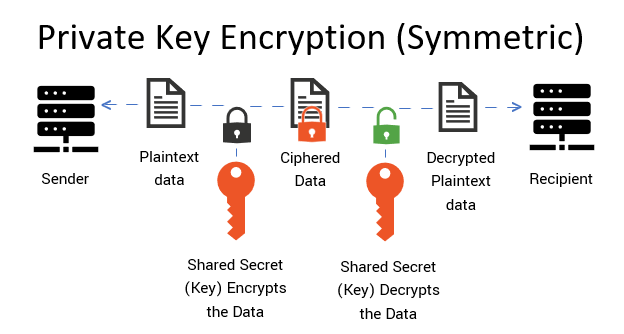
At its core, a private key is a clandestine string of alphanumeric characters that pairs with a public key to enable secure communication and data encryption. The efficacy of private key cryptography hinges on a carefully calibrated balance of computational complexity and secure storage. The vast majority of private key systems employ algorithms that are inherently resistant to brute-force attacks, yet the mere act of having a strong key cannot assure unfaltering security. What then makes a private key secure, and how do hackers strategize to commandeer it?
To grasp the essence of private key security, one must first comprehend the cryptographic algorithms in play. Algorithms such as RSA and Elliptic Curve Cryptography (ECC) bolster key security through mathematical underpinnings that might seem arcane to the layperson. Essentially, these algorithms transform a simple piece of data into an intricate tapestry of characters that can only be unraveled through the correct private key. However, as any seasoned locksmith knows, the vulnerability often lies not in the lock, but in the vicinity surrounding it.
The distribution and storage of private keys evoke vivid metaphorical imagery. Think of a private key as an ancient scroll that contains the secrets to an enchanted realm. If that scroll is kept in a secure library deep within the castle’s walls, it remains protected. However, if the scroll is casually left on a desk in a bustling tavern, any opportunistic rogue lurking nearby can snatch it away. Thus, the physical and digital environments where private keys reside must be safeguarded against unauthorized access.
For hackers—modern-day marauders—the quest to steal private keys is a pursuit that can be achieved via a myriad of nefarious tactics. One prevalent method is through phishing attacks, which function much like a con artist’s ploy to lure unsuspecting victims. Hackers often craft deceptive e-mails that masquerade as legitimate messages from trusted entities, enticing users to divulge their private key credentials. Once a hacker successfully tricks an individual into providing this invaluable information, they gain unfettered access to the victim’s assets.
Another striking analogy can be drawn between private key security and urban fortification. Consider a city with towering walls, yet a lack of vigilant guards. This reflects an environment where private keys might be stored on devices that are vulnerable to malware or spyware. Malware operates surreptitiously, surreptitiously stealing sensitive information, including private keys, while users remain oblivious to the encroaching threat. By the time the victim realizes the danger, it is often too late—much like realizing a city has been infiltrated only after the damage has been done.
Moreover, the phenomenon of social engineering cannot be overlooked. This tactic exploits human psychology rather than technological vulnerabilities. Hackers may impersonate IT personnel, coaxing individuals into revealing their private keys under the guise of conducting a systems check. This technique illustrates the point that, at times, no significant hacking skill is required—just the manipulative art of persuasion.
As we delve deeper into the realm of cryptography, it becomes evident that the landscape is constantly evolving. Emerging technologies, such as quantum computing, pose a new frontier that could potentially unravel the very foundations upon which private key security relies. Quantum computers possess the capability to execute complex calculations at unprecedented speeds, raising alarms about the potential obsolescence of current cryptographic algorithms. It is imperative for security experts to explore quantum-resistant algorithms that could withstand the looming quantum onslaught.
In response to these multifaceted threats, the implementation of multi-factor authentication (MFA) is becoming increasingly vital. This security technique adds layers of protection by requiring users to provide two or more verification factors before gaining access to sensitive data. By enhancing the security framework, MFA acts as a formidable bulwark, fortifying the castle walls and deterring potential invaders.
Furthermore, the adage “knowledge is power” rings true in the context of private key security. Organizations and individuals must engage in ongoing education regarding the latest advancements in cybersecurity, evolving threats, and the best practices for safeguarding keys. The implementation of regular audits, comprehensive user training, and fostering a culture of vigilance can significantly reduce vulnerabilities that hackers exploit.
The intricate relationship between private key security and cybersecurity illustrates a dynamic interplay that is continuously evolving. As hackers refine their techniques to breach defenses, cryptographers and security professionals must remain vigilant, innovating and fortifying their strategies. Ultimately, the security of private keys requires not just robust cryptographic algorithms, but also an unwavering commitment to protecting these keys from the relentless pursuit of those who seek to commandeer them. In this unending battle between protectors and invaders, the only certainty is change—and the imperative of proactive defense.







Leave a Comment