Cryptography, a term that resonates deeply within the corridors of computer science, serves as a bulwark against the inexorable tide of data insecurity. Its usage transcends the mere safeguarding of passwords, delving into a plethora of applications that are integral to our digital existence. This exploration seeks to elucidate the multifaceted dimensions of cryptography, unveiling its significance in various realms of computer science—an unassuming yet vital cog in the machinery of technological progress.
At its core, cryptography is the art and science of encoding and decoding information. Picture it as a sophisticated lockbox, where only those possessing the key can access its contents. This metaphor—the lock and key—provides an accessible illustration; however, the intricate mechanisms underpinning cryptography are far more complex. Beyond the foundational role of securing passwords, cryptography introduces a suite of methods for ensuring the integrity, confidentiality, and authenticity of data.
One of the most emblematic applications of cryptography is in the realm of secure communications. The proliferation of digital communication platforms necessitates ironclad security measures. Here, cryptographic protocols like Secure Socket Layer (SSL) and Transport Layer Security (TLS) come into play. These cryptographic technologies serve to encrypt data transmitted over the internet, ensuring that eavesdroppers cannot easily intercept or tamper with the information exchanged between servers and clients. This process is akin to transmitting messages via a securely sealed envelope rather than through a postcard, safeguarding sensitive information from prying eyes.
Moreover, the concept of public key infrastructure (PKI) enhances this secure communication framework by introducing a dual-key mechanism—a public key for encryption and a private key for decryption. Visualize this scenario: each participant in a conversation possesses an open lock (the public key) that anyone can use to drop in a message but only the lock’s owner holds the corresponding key (the private key) to retrieve it. This system allows for a robust and secure communication channel, enabling entities to exchange information securely without pre-existing shared secrets.
Cryptography also plays a pivotal role in ensuring data integrity, a critical requirement for various applications including software distribution and financial transactions. Hash functions are employed for this very purpose, generating unique fingerprints for data sets. These cryptographic hash functions produce fixed-size outputs commonly referred to as hash values. Imagine a bouncer checking IDs at a venue entrance; if the ID matches the visitor’s expectations, they gain access. Similarly, hash values enable systems to verify the integrity of data by comparing calculated hashes against known values. Any alteration in the data will result in a disparate hash, signaling possible tampering or corruption.
Another vital application of cryptography is in digital signatures, which authenticate the identity of the sender and affirm that the message has not been altered in transit. This is analogous to the age-old practice of signing a letter; however, the modern implementation ensures authenticity through sophisticated mathematical algorithms. When a sender’s digital signature is affixed to a piece of data, it serves as a beacon of trust, allowing recipients to verify not only the identity of the sender but also the integrity of the message. Digital signatures have gained prominence in legal agreements, securing sensitive transactions, and facilitating electronic voting systems.
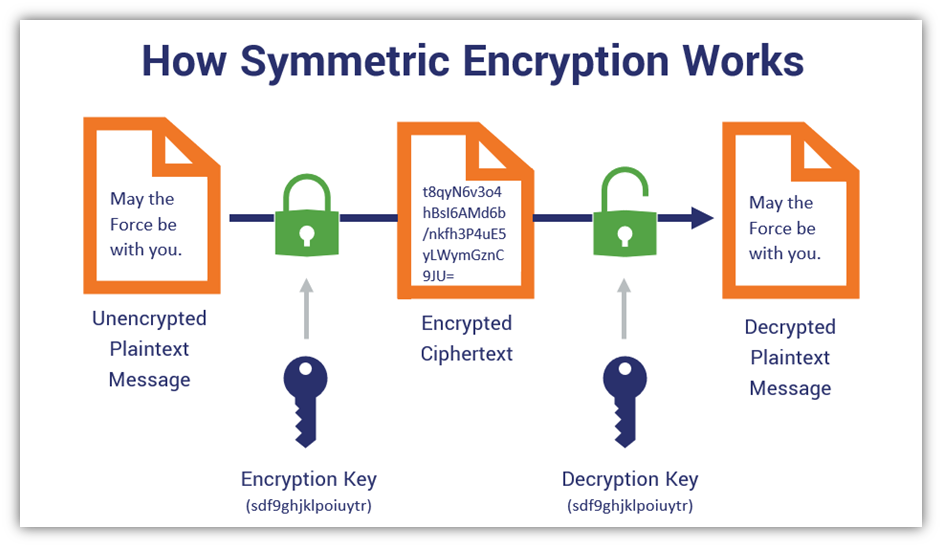
The compound necessity for privacy protection has fostered advancements in cryptographic techniques, particularly through the lens of symmetric and asymmetric encryption. Symmetric encryption, where the same key is wielded for both encryption and decryption, offers expediency when handling large volumes of data. Visualize a single master key that opens multiple doors, revealing treasures safely tucked away inside. Conversely, asymmetric encryption, while resource-intensive, provides an elegant solution that underpins secure communications without the need to share secrets in advance. By using a pair of keys, it elevates security protocols to exceptional standards, mitigating risks associated with key distribution.
In a world growing increasingly reliant on data anonymity, cryptography’s role extends to preserving user privacy. This is poignantly evident within the frameworks of cryptocurrencies, which utilize cryptographic algorithms to enable secure, anonymous transactions. Blockchain technology, a byproduct of cryptography, catalyzes this evolution by providing an immutable ledger that ensures the transparency and traceability of transactions. Here, each transaction can be likened to a well-guarded vault—a series of interconnected vaults (blocks) storing valuable information, all tethered through cryptographic links that prevent tampering.
Furthermore, the burgeoning field of quantum cryptography introduces an innovative perspective on data security. By leveraging the principles of quantum mechanics, this cutting-edge approach holds the potential to revolutionize the way we conceive encryption. Imagine an impenetrable fortress, constructed not with physical barriers, but with the delicate laws of nature—this is the vision that quantum cryptography aims to realize. It promises unparalleled levels of security through quantum key distribution (QKD), where any attempt to eavesdrop is immediately detectable due to the nature of quantum particles.
In closing, the vast implications of cryptography extend far beyond the realm of safeguarding passwords. It serves as the backbone of secure communications, data integrity, authentication, and privacy. The intricate tapestry woven by various cryptographic applications reveals a landscape rife with innovation and necessity. As technology continues to evolve, the role of cryptography will undoubtedly expand, adapting to meet the security challenges posed by a progressively digital world. In this dance of encryption and decryption, the future of secure technology holds immense potential, driven by the relentless pursuit of safeguarding our most sensitive information.






Leave a Comment