Imagine this: you’ve just left the ATM after withdrawing cash. As you reach into your pocket, your ATM card slips through your fingers and tumbles to the ground. What if a stranger picked it up? Would they be able to access your account? This playful scenario poses a serious question: how does cryptography safeguard your ATM card information, especially if it is lost or stolen?
The significance of cryptography in protecting financial transactions cannot be overstated. Cryptography is a field dedicated to the principles and techniques of securing information. It employs mathematical algorithms to encrypt data, ensuring that only authorized entities can access it. This essay investigates the various mechanisms employed in ATM card security, a battleground where cryptographic techniques play a crucial role.
To truly appreciate the efficacy of cryptography in ATM cards, one must first understand what these cards contain. An ATM card is equipped with a magnetic stripe or a chip, which stores sensitive information including your account number, card expiration date, and dropdown security codes. In the hands of an unscrupulous individual, this information could lead to unauthorized transactions. Thus, the importance of an encrypted, secure transmission of data becomes exceedingly clear.
The first layer of protection lies in the form of encryption techniques utilized during communication between your ATM card and the ATM itself. When you insert your card into the terminal, the card’s chip or magnetic stripe and the terminal engage in a dialogue embedded in cryptographic language. This exchange must remain confidential, and thus encryption is employed to obfuscate the data.
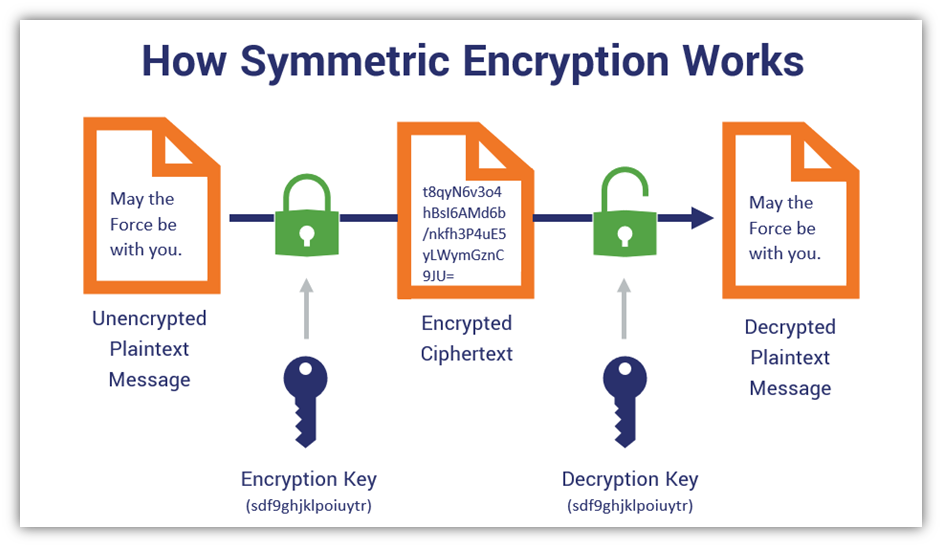
When your card is swiped, the terminal generates a unique transaction code. This code is time-sensitive, meaning it is invalidated after a brief period. In tandem with this, the card generates a cryptographic key specific to this transaction, employing an advanced cryptographic technique called symmetric encryption. Symmetric encryption uses a single key to encrypt and decrypt data. The ATM and the issuing bank both possess copies of this key but don’t share it outwardly. This ensures that even if a malicious user intercepts the data during transmission, they are likely unable to decrypt it without access to the key.
However, a card’s vulnerabilities do not fade away with transmission encryption alone. A second line of defense is provided by the use of EMV chips, which were designed to enhance security and reduce fraud. EMV, which stands for Europay, MasterCard, and Visa, signifies a standard for integrated circuit cards. Unlike traditional magnetic stripes, EMV chips use dynamic authentication. Each time the card is used in a transaction, it generates a unique cryptographic signature for that transaction, rendering any replicated data from past transactions useless to a potential fraudster.
Now, consider a scenario where you drop your card, and an ethical question arises: should the person who finds it attempt to return it or use it to exploit your financial resources? Despite the moral implications, could they carry out the latter action? This is where a sophisticated security measure—tokenization—comes into play. Tokenization is an advanced cryptographic process that replaces sensitive data with non-sensitive equivalents, called tokens. In the case of an ATM card, tokenization means that even if someone obtains your account number, they cannot perform transactions without additional identifiers stored securely with the issuing bank.
Moreover, the deployment of transaction limits adds another layer of complexity to ATM security. Banks often impose cash withdrawal limits on accounts. Even if an individual who finds your card attempts to withdraw cash, these limits thwart significant financial damage. Coupled with this, banks monitor transaction patterns using machine learning algorithms to flag suspicious activities, such as unusually large or out-of-pattern withdrawals—further protecting your assets.
However, these security measures are not foolproof. Cybercriminals are continuously evolving, employing sophistication that can outpace conventional security practices. Therefore, users should remain vigilant. Maintaining a secure PIN is essential, as it is the final piece in the cryptographic puzzle that protects your account. Using a PIN that is complex, unique, and changed regularly adds further strength to your account’s defense.
Moreover, two-factor authentication (2FA) steps in as a formidable ally in the landscape of ATM security. By requiring a second form of verification—for instance, a temporary code sent to your mobile device—2FA ensures that even if a thief gathers both your ATM card and your PIN, your account remains safely out of their reach.
In conclusion, the symbiotic relationship between cryptography and ATM card security is intricate and multifaceted. While the playful scenario of a dropped card and an opportunistic finder presents real concerns, the various strategies—encryption, EMV chip technology, tokenization, transaction monitoring, and 2FA—exemplify a strong defense against potential fraud. While no system guarantees absolute security, the current landscape overwhelmingly illustrates that cryptographic solutions significantly mitigate risks, allowing you to rest easier whenever you retrieve cash from an ATM. With the continued advancements in this field, one can only expect further enhancements that will keep financial data secure even in our rapidly evolving digital age.







Leave a Comment