In today’s digital age, messaging apps have become ubiquitous. They facilitate communication across vast distances, yet a fundamental question lingers: how secure are these conversations? At the heart of this inquiry lies the concept of encryption. For the uninitiated, the term often conjures images of secret codes and spies, yet the reality is more intricate and significant. Diving into the intricacies of how messaging apps use encryption to secure text messages reveals how an understanding of this technology can shift our perspective on privacy and security.
Encryption is a method of protecting information by transforming it into an unreadable format for anyone who does not possess the correct decryption key. At its essence, encryption safeguards the confidentiality of our digital conversations. In common messaging platforms, this process typically employs complex algorithms designed to prevent unauthorized access. Thus, even if a malicious entity were to intercept a message, it would be meaningless without the requisite cryptographic key.
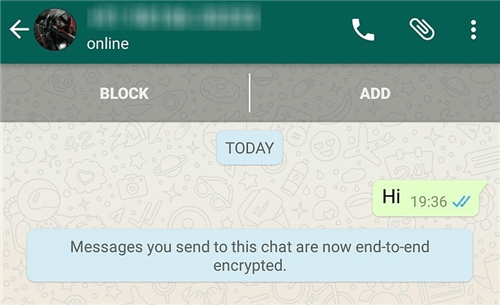
Most contemporary messaging applications utilize a methodology known as end-to-end encryption (E2EE). This framework exemplifies a promise made by these applications: only the communicating users can read the messages. Not even the service providers can decipher the contents. This promise is at the core of user trust; knowing that only the sender and the recipient can interpret what is exchanged lends a sense of security absent in unencrypted platforms.
To illustrate how this system functions, consider the transmission process. When a user sends a message, their device employs a key to encrypt the text. This transformation converts the plain text into ciphertext, a series of seemingly random characters. For instance, the simple message “Hello” might transform into something resembling “Wb1$^b3*Fc9”. To decrypt this message, the recipient’s device requires a corresponding key, enabling it to revert the ciphertext back to its original form.
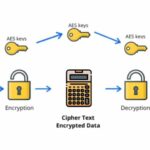
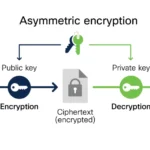
Key generation is a critical facet of the encryption process. Different applications employ varying strategies, such as symmetric or asymmetric encryption. Symmetric encryption uses the same key for both encryption and decryption, necessitating secure key sharing between users. In contrast, asynchronous methods leverage a pair of keys – a public key for encryption and a private key for decryption. This discrepancy enhances security since the public key can be shared openly without compromising the private key.
To grasp the significance of end-to-end encryption, one must consider the threats posed in the absence of such security measures. Cybercriminals often lurk in the shadows of the internet, employing tactics like intercepting data packets as they traverse the network. Without robust encryption, messages can be easily captured, leading to data breaches and identity theft. With E2EE, even if hackers intercept the data, they receive nothing more than an incomprehensible string of characters.
However, the conversation around encryption is not devoid of ethical considerations. While end-to-end encryption promotes security, it also poses challenges for law enforcement agencies. Blocks of potential evidence may remain inaccessible during investigations due to the very safeguards that protect user privacy. This paradox raises an essential question: should the right to privacy supersede the need for security and justice? The conversation around encryption continues to evolve as authorities, technologists, and civil liberties advocates debate the balance necessary to maintain both security and privacy.
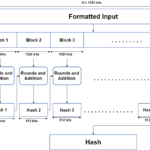
The intricacies of encryption can elicit curiosity about the algorithms at play. One popular algorithm used in messaging applications is the Advanced Encryption Standard (AES). AES encrypts data in block sizes of 128 bits, employing key sizes of 128, 192, or 256 bits, enhancing security exponentially with each increase in bit size. The complexity of these algorithms serves as a deterrent against brute-force attacks, where attackers aim to guess the key by trying numerous combinations until they succeed.
Another concept that warrants exploration is the role of metadata. Many users assume that encryption solely protects the contents of messages. However, metadata—which includes details like timestamps, sender and receiver information, and message size—often remains visible. Hence, while the content may be secure, the metadata can still reveal patterns and contexts that can be exploited by malicious actors. The transparency of this information underscores the need for a comprehensive understanding of secure communication, where both content and metadata deserve scrutiny.
As we continue to navigate the complexities of digital communication, the continual evolution of encryption technology remains critical. Innovations like quantum encryption are on the horizon, promising to push encryption to unprecedented levels of security. Yet, as new encryption methodologies emerge, so do new vulnerabilities and threats. Cybersecurity is a moving target; what is invulnerable today may become obsolete tomorrow. This relentless evolution cultivates an environment where individuals must stay informed, adaptive, and vigilant in their online communications.
Ultimately, understanding how messaging apps encrypt texts is more than a matter of curiosity; it’s imperative for ensuring personal privacy and security in an interconnected world. The promise of E2EE challenges us to rethink our approaches to online communication while urging us to advocate for privacy rights. In an age where information is power, recognizing these technologies’ capabilities and limitations is essential for making informed decisions about our digital interactions.
In conclusion, as messaging apps continue to permeate everyday life, the encryption of our communications safeguards our right to privacy. Whether discussing mundane events or sensitive information, encryption stands as a bulwark against prying eyes. By understanding how these processes work, individuals can appreciate the value of secure communication—a foundation upon which the future of digital interaction rests.




Leave a Comment