In an increasingly digital era, where online interactions often replace traditional face-to-face communication, the concept of web trust arises as paramount. Without a modicum of trust, the Internet could devolve into a chaotic environment rife with deception and malfeasance. The question that beckons is: can we ever fully trust the web? A tantalizing challenge emerges: how do we ensure security, identity verification, and data integrity in a nebulous digital landscape? Enter digital certificates—an intricate yet indispensable mechanism that underpins the foundation of web trust.
To understand the role of digital certificates, it is crucial to grasp the underlying architecture of secure web communication. At the heart of this structure lies the Secure Socket Layer (SSL) and its successor, Transport Layer Security (TLS). These protocols facilitate encrypted communication between users and servers, ensuring that sensitive data remains private and untampered. However, encryption alone does not suffice. The digital certificate acts as a catapult toward verification, a foundational piece in establishing the authenticity of a website.
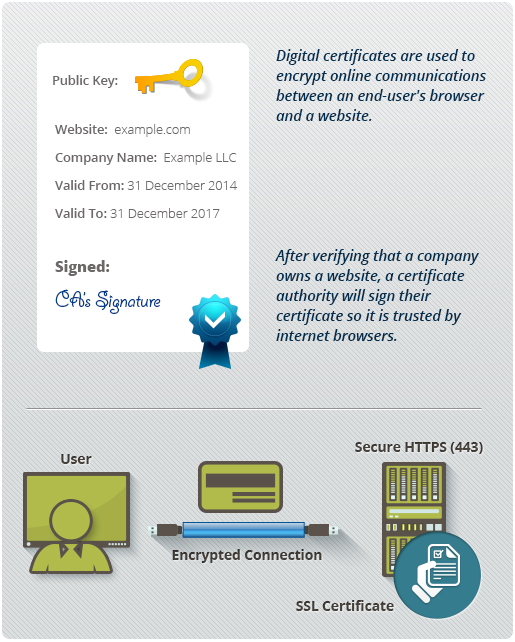
A digital certificate serves as an electronic credential, analogous to an online passport. Issued by a Certificate Authority (CA), it corroborates the identity of an entity in the digital domain. When a user endeavors to connect to a secure website, the server presents its digital certificate. This document contains critical information: the website’s public key, the identity of the certificate holder, the expiration date, and the CA’s digital signature. This intricate ballet of data exchange ensures that the user is indeed communicating with the intended party and not an imposter masquerading as a legitimate entity.
However, one must consider: what if the CA itself is compromised? The integrity of the entire digital certification system could unravel, allowing malicious entities to impersonate trusted organizations. As our reliance on web trust grows, so does the imperative for CAs to maintain robust security measures. The potential for a single point of failure presents an ongoing challenge that calls for vigilance, innovation, and collaboration within the cybersecurity community.
A pivotal aspect of digital certificates is their role in public key infrastructure (PKI). PKI not only safeguards encrypted transactions but also establishes a hierarchical relationship between CAs and end-user devices. This framework allows for the decentralization of trust—rather than relying solely on a single entity, trust is distributed across numerous CAs. Thus, the demise of one CA does not extinguish the trust afforded by others; the web remains resilient against the challenges of maleficence.
Moreover, digital certificates are not merely a technical fiat; they are a psychological assurance to users. A small padlock icon in a browser’s address bar connotes a sense of safety. Consumers gravitate toward websites that display such assurances. A study conducted by various cybersecurity experts highlighted that a significant percentage of users abandon purchases on sites lacking visible security features. This phenomenon elucidates the symbiotic relationship between digital certificates and commerce; businesses that neglect to procure valid certificates risk losing customer trust and, ultimately, revenue.
Yet, as secure as they may seem, digital certificates are not immune to obsolescence. The advent of quantum computing looms like a specter over the realm of cryptography. Current encryption algorithms, upon which digital certificates rely, may become feeble against the computational prowess of quantum machines. Cryptographic experts grapple with this impending challenge, seeking more robust algorithms to future-proof digital communication. The proactive measures undertaken now will dictate the era of secure web transactions for decades to come.
It is incumbent upon each organization to recognize the gravity of digital certificates. The procurement and renewal of certificates must be treated with the utmost diligence. Organizations should implement automated systems for monitoring certificate status and commit to maintaining transparency around their certificate management practices. A lapse in vigilance could lead to expired certificates, rendering a site vulnerable to attack and eroding consumer confidence.
Additionally, regulatory frameworks are beginning to reflect the importance of digital certificates in establishing web trust. Legislations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) necessitate that organizations adopt rigorous security measures. Digital certificates not only serve as protective shields but also align organizations with best practices as prescribed by evolving legal standards. Thus, digital certificates are not only a technical requirement; they are emerging as critical components of regulatory compliance.
As we traverse the multifaceted domain of web trust, it becomes evident that digital certificates are not mere accessories to online security—they are the very bedrock upon which trust is built. They nurture a symbiotic relationship between security, user psychology, and regulatory compliance. As technology continues to evolve, the discourse surrounding digital certificates must adapt, encouraging innovation and vigilance among all stakeholders. How, then, will you arm yourself with knowledge in the face of an ever-changing digital landscape? As we continue to explore the potential pitfalls and triumphs of technology, the capacity to safeguard our digital identity lays foundationally upon robust mechanisms like digital certificates.








Leave a Comment