Public key signing is a fundamental process in the realm of cryptography that ensures the integrity, authenticity, and non-repudiation of digital communications. It serves as a keystone for various applications, enabling entities to sign data securely while maintaining transparency and authenticity. This article delves deeply into public key signing, exploring its mechanisms, applications, and the meticulous process involved in signing data.
At the heart of public key signing lies asymmetric cryptography, which employs a dual key system — a public key and a private key. The public key is disseminated widely, while the private key is kept confidential by the owner. This asymmetry creates a secure framework, wherein a signer uses their private key to produce a digital signature, and anyone with the corresponding public key can verify that signature. This verification process serves as a robust proof mechanism, confirming both the origin of the data and its integrity.
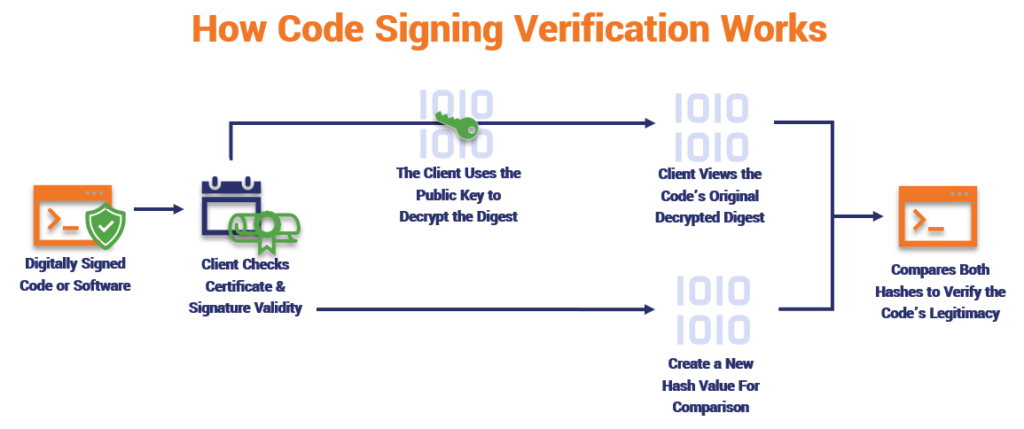
To comprehend the efficacy of public key signing, one must first understand the critical function of digital signatures. A digital signature is akin to a handwritten signature or a stamped seal, but it offers far greater security. When data is signed using a private key, it generates a unique hash value — a fixed-size string of characters derived from the original data. This hashing process ensures that even the slightest alteration to the data would result in a completely different hash value upon re-computation. Subsequently, the hash is encrypted with the signer’s private key to form the digital signature. This signature, along with the original data, can then be sent to the recipient.
The verification process initiates when the recipient receives the signed data. Utilizing the issuer’s public key, the recipient can decrypt the signature to retrieve the original hash value. Subsequently, the recipient hashes the received data and compares it to the decrypted hash value. If both values align, it affirms that the data remains untampered and authentic, having originated from the claimed sender. This seamless operation underscores the significance of utilizing public key infrastructure (PKI) to manage and distribute public keys securely.
Various types of content can be signed using public key signing techniques. These include documents, emails, software applications, and even blockchain transactions. Each application carries its nuances, demonstrating the versatility of digital signatures. For instance, in software distribution, public key signing ensures that users download authentic applications free of malware and unauthorized modifications. Developers sign their software with a private key, allowing users to verify the authenticity before installation.
Email authentication has gained prominence with the advent of standards like DKIM (DomainKeys Identified Mail). This mechanism employs the sender’s private key to create a signature for outgoing messages. When the message is received, the recipient’s email server can verify the signature using the sender’s public key, thus mitigating the prevalent issues of email spoofing and phishing attacks.
However, while public key signing brings myriad benefits, it is not devoid of challenges. The security of the entire process hinges on the protection of the private key. If the private key is compromised, any data signed with it becomes vulnerable, potentially allowing malicious entities to impersonate the signer or manipulate data undetected. Consequently, implementing secure key management practices becomes paramount. Organizations must adopt rigorous security measures to protect private keys, including utilizing hardware security modules (HSM) and multifactor authentication methods.
Moreover, the efficacy of public key signing is contingent upon the trustworthiness of the public key’s source. This is where the role of Certificate Authorities (CAs) comes into play. CAs issue digital certificates that authenticate the ownership of a public key, establishing trust in the key’s origin. The chain of trust established by CAs is pivotal in fostering confidence in digital transactions, particularly in sensitive environments such as financial services and healthcare.
In addition to traditional applications, the significance of public key signing has been accentuated with the proliferation of blockchain technology. Each transaction in a blockchain is signed using the private key of the sender, ensuring that only the rightful owner can enact modifications. This decentralized approach not only enhances security but also provides transparency; all transactions can be viewed and verified by participants on the blockchain without revealing private keys.
Furthermore, the concept of timestamping can be integrated with public key signing to enhance accountability. By embedding timestamps within digital signatures, the signer can assert the existence of data at a specific point in time. This becomes particularly relevant in legal contexts, where proving the timing of document creation or modification is crucial.
In conclusion, public key signing is an indispensable technology that fortifies communication and data integrity across various domains. Its transformative capabilities, coupled with the robustness of asymmetric cryptography, ensure that individuals and organizations alike can engage in secure and transparent digital interactions. Yet, as public key signing becomes increasingly integrated into everyday technology, the necessity for vigilant security practices and authenticating frameworks persists. Through continued advancements and awareness, the integrity of public key signing can be safeguarded, fostering trust in the digital landscape.







Leave a Comment