In a world increasingly dominated by digital interactions, the concept of data integrity is paramount. Just as a vault preserves precious artifacts from decay and theft, digital signatures safeguard electronic data from tampering. Picture a digital signature as an impenetrable seal affixed to a letter—if the letter is opened, the seal breaks, revealing that the contents have been tampered with. This metaphor captures the essence of how digital signatures function.
To delve deeper, let’s first dissect the components of a digital signature. At its core, a digital signature employs cryptography—an ancient art of encoding messages to protect their confidentiality and integrity. Cryptography is akin to a secret language, understood only by the sender and intended recipient. However, digital signatures go beyond mere confidentiality; they ensure that the information has not been altered during transmission, akin to a wax seal confirming the authenticity of a royal document.
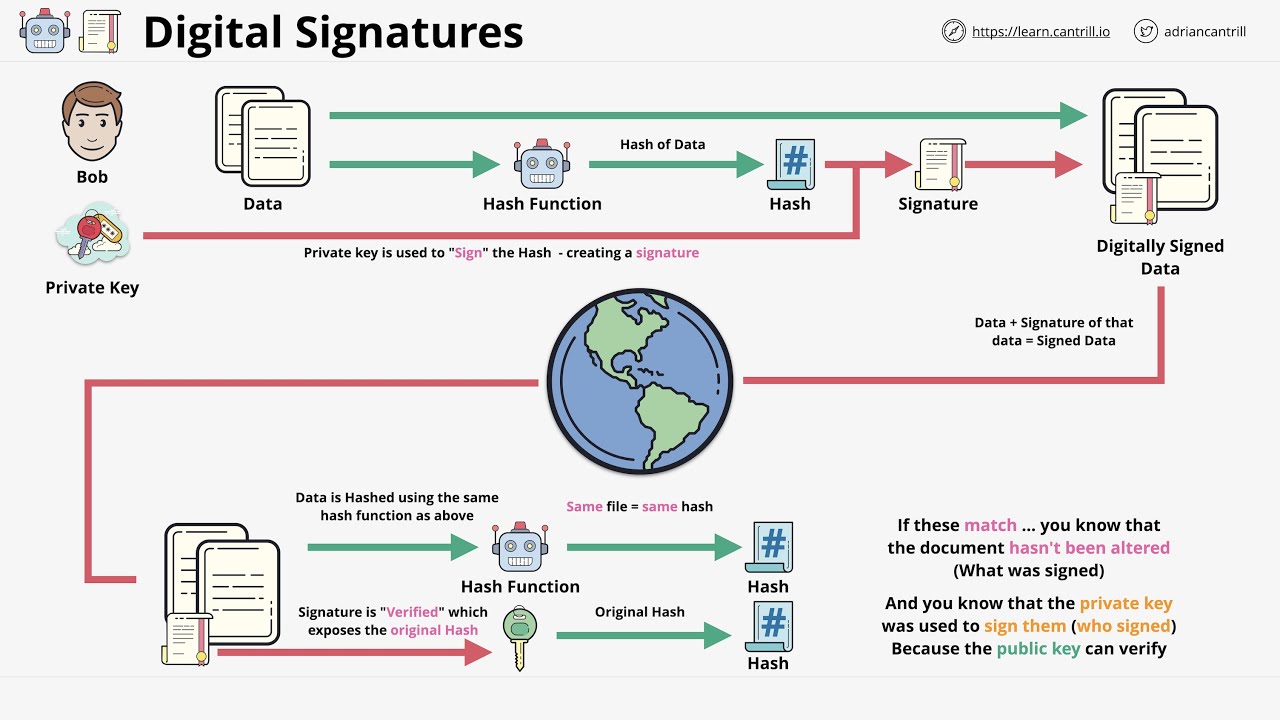
The process begins with hashing. A hash function transforms data into a fixed-length string of characters, irrespective of the original data’s size. Consider this as reducing an elaborate painting to a mere fingerprint; it encapsulates the essence of that painting while being substantially smaller in size. The beauty of this fingerprint lies in its uniqueness—similar to a snowflake, it possesses distinctive features that are incredibly unlikely to be replicated, providing a robust foundation for data integrity.
Once the data has been hashed, the next step is the application of asymmetric encryption. This dual-key system involves a public and a private key—one acts as a lock, while the other serves as its counterpart. The private key, likened to a unique combination that only the sender knows, is used to encrypt the hash. This encrypted hash then forms the digital signature, which is sent along with the original data. The public key acts as the universal key that anyone can use to decrypt the signature, ensuring that any recipient can verify the authenticity of the data.
Upon receiving the signed data, the recipient must perform two critical steps to validate its integrity. Firstly, the recipient uses the sender’s public key to decrypt the digital signature, revealing the hash of the original data. Secondly, the recipient employs the same hash function on the received data, generating a new hash. If these two hashes match, it serves as an undeniable proof that the data has remained unchanged. Thus, the digital signature functions as a guardian, ensuring the purity of the data and providing assurance against unwarranted alterations.
The allure of digital signatures extends beyond mere technical functionality; they embody a broader societal need for trust in digital communications. Trust is akin to the glue that bonds relationships, and in the realm of electronic transactions, it ensures that parties can engage in business confidently, knowing that they are not subject to deceit. For instance, online banking relies heavily on digital signatures. When you authorize a transaction, your digital signature verifies your consent, safeguarding your financial data and affirming that it is indeed you behind the curtain.
Moreover, in realms such as e-commerce, digital signatures play a pivotal role in enhancing security. Imagine a merchant who signs a digital receipt. This act not only confirms the transaction but also bolsters the buyer’s assurance that the merchant is legitimate. If the signature is valid, the consumer can proceed with their purchase without the specter of fraud lurking in the shadows. Here, digital signatures act as a lighthouse, guiding consumers through the treacherous waters of online shopping.
However, the journey of digital signatures is not devoid of challenges. Cybercriminals, akin to cunning thieves, constantly devise methods to bypass security mechanisms. Techniques such as spoofing or man-in-the-middle attacks attempt to undermine the integrity provided by digital signatures. This is where the importance of using robust cryptographic standards becomes apparent. Digital signatures must evolve alongside threats, ensuring that they remain secure against evolving cyber threats. Utilizing advanced algorithms and regularly updating cryptographic practices is critical in maintaining the integrity of digital signatures.
In conclusion, digital signatures are instrumental in the preservation of data integrity in our digital landscape. They act as vigilant sentinels, ensuring that information remains untarnished during transmission. By employing hashing and asymmetric encryption, they provide an unassailable method for verifying data authenticity. As society continues to navigate the realm of digital communication, the value of trust cannot be overstated. Digital signatures solidify this trust, enabling individuals and businesses to interact securely, promoting a culture of transparency and accountability. Just as a time-tested vault protects treasures, digital signatures defend our valuable data against the perils of alteration and deceit, emblematic of a broader commitment to safeguarding integrity in the digital age.








Leave a Comment