In the digital age, the notion of signing documents has transcended traditional ink and paper methods, evolving into a sophisticated mechanism known as digital signatures. This transformation sparks intrigue within many, as it challenges conventional perceptions of authenticity and legal agreements. Understanding how digital signatures function delves into the intersection of cryptography and legal frameworks, revealing why they are regarded as legally binding.
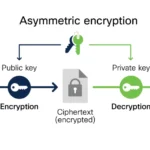
At its core, a digital signature serves as a unique identifier, akin to a handwritten signature or a stamped seal, but with a significant technological underpinning. This process begins with cryptographic techniques, primarily utilizing asymmetric encryption. This method relies on a pair of keys: a private key known only to the signer and a public key that is shared with anyone wishing to verify the signature. The interplay between these two keys lies at the heart of digital signature technology.
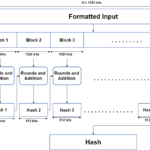
When an individual decides to sign a document digitally, they generate a hash—a compact representation of the document’s content—using a cryptographic hash function. This hash serves as a digital fingerprint of the document, ensuring that any alterations made to the document post-signature can be detected. The hash is then encrypted with the signer’s private key, resulting in the digital signature itself.
Once the digital signature is created, the complete document and the signature are transmitted to the recipient. To authenticate the signature, the recipient utilizes the corresponding public key to decrypt the signature back into the hash. Concurrently, they generate their own hash of the received document. If these two hashes align perfectly, it serves as corroborative evidence that the document remains unaltered and verifies the identity of the signer.
This mechanism is not merely a technical marvel; it bridges the gap between digital interactions and the legal principles governing contracts. For a digital signature to be considered legally binding, it must comply with specific regulations and standards established by laws such as the Electronic Signatures in Global and National Commerce (ESIGN) Act in the United States and the eIDAS Regulation in the European Union. These laws affirm that electronic signatures hold the same legal weight as traditional signatures, provided certain criteria, such as intent and consent, are met.
The allure of digital signatures can be attributed to their capacity for enhancing security and efficiency in transactions. In an increasingly interconnected world, the ability to securely sign documents without the constraints of physical proximity is not just convenient; it reflects a transformative shift in how business is conducted. Organizations and individuals benefit from reduced turnaround times, decreased reliance on paper, and enhanced tracking capabilities.
However, despite their convenience, a deeper inquiry into the implications of digital signatures raises pertinent questions. As reliance on digital tools grows, so does the potential for cyber threats. Identity theft, phishing attacks, and other malicious activities pose significant risks that can undermine the integrity of digital signatures. Consequently, best practices for safeguarding private keys and employing robust encryption methods become paramount in preserving the sanctity of electronic agreements.
Furthermore, examining the psychological dimensions of digital signatures reveals an intriguing dichotomy. For some, the idea of signing electronically may seem less personal or concrete compared to the tactile experience of a wet signature. This sentiment often arises from a lack of familiarity with digital technologies and the trust issues inherent in electronic interactions. Building confidence in the digital signature process necessitates thorough educational initiatives and user-friendly platforms that instill faith in this technology.
Legal ramifications surrounding digital signatures further accentuate the necessity for comprehensive understanding. Courts have increasingly upheld the enforceability of digital signatures, reinforcing their legitimacy in legal contexts. Nonetheless, disputes may arise regarding the authenticity of a signature, especially if there remains ambiguity about the identity of the signer or the conditions under which the document was executed. Such dilemmas underscore the imperative for meticulous record-keeping and transparent procedures throughout the signing process.
As we traverse the digital landscape, one cannot overlook the philosophical implications of our evolving relationship with technology and signatures. The traditional notions of trust, authenticity, and personal connection are being redefined. A digital signature, while inherently secure, raises questions about the nature of consent and the extent to which technology influences our interactions. This evolution mirrors broader societal changes, reflecting our adaptation to an increasingly digital-centric vision of reality.
In conclusion, digital signatures represent a confluence of advanced technology and legal principles, offering a unique lens to explore the complexities of modern communication. Their functionality, rooted in cryptographic techniques, provides a secure method for verifying identity and ensuring the integrity of documents. As their use continues to proliferate across various sectors, it becomes crucial to address the associated risks and foster an environment of trust. The legal standing of digital signatures is well-established; however, ongoing dialogue about their implications ensures that they are integrated thoughtfully within the frameworks of our society. Such discourse not only enhances understanding but also fortifies the foundation upon which future digital interactions will be built.





Leave a Comment