Public key cryptography is a seminal component of modern secure communication systems. Central to its functioning is key management, which involves the generation, distribution, storage, use, and revocation of cryptographic keys. This article delves into how key management works in public key cryptography, elucidating its various facets while exploring the responsibilities and challenges that accompany it.
Understanding Public Key Cryptography
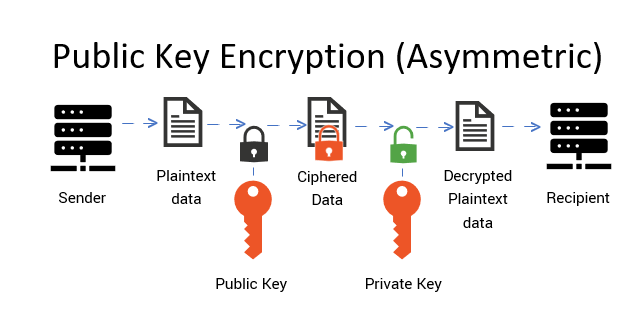
At the heart of public key cryptography lies the concept of asymmetric key pairs, which consist of a public key and a private key. The public key, as its name implies, can be disseminated openly, while the private key remains confidential to the owner. This duality allows for distinctive operations; encryption with a public key can only be decrypted by the corresponding private key, ensuring a robust level of secrecy. Similarly, a digital signature created with the private key can be verified using the public key, thereby fostering authenticity and non-repudiation.
The Essentials of Key Management
Key management encompasses several critical activities that ensure effective governance over cryptographic keys. These activities can be broadly categorized into key generation, key distribution, key storage, key usage, key rotation, and key revocation. Each phase presents its own challenges and requires meticulous implementation to safeguard sensitive information.
1. Key Generation
The first step in key management involves the secure creation of key pairs. Public key algorithms, such as RSA or ECC (Elliptic Curve Cryptography), utilize complex mathematical computations to generate these keys. The security of the keys lies not merely in the algorithm’s design but also in the randomness of the key material. A strong random number generator is crucial, as predictable keys can lead to vulnerabilities that malicious actors could exploit.
2. Key Distribution
Once generated, public keys need to be distributed to legitimate parties in a manner that guarantees their integrity. This is often accomplished through Public Key Infrastructures (PKIs), which establish frameworks that authenticate identities and manage key distributions through digital certificates. Certificates are issued by trusted Certificate Authorities (CAs), which validate the ownership of public keys, thereby mitigating risks associated with man-in-the-middle attacks.
3. Key Storage
The security of private keys depends heavily on their storage methodology. These keys must remain confidential and protected from unauthorized access. A variety of storage solutions exist, ranging from secure hardware devices such as Hardware Security Modules (HSMs) to encrypted file systems. Each solution carries its own benefits and drawbacks concerning accessibility, performance, and cost. Hence, organizations must evaluate their specific needs to determine the most appropriate method for private key storage.
4. Key Usage
Key usage pertains to the actual application of the generated keys within cryptographic processes. This involves encryption, decryption, signing, and verification operations. Organizations must adopt strict access controls and policies governing how keys can be utilized to prevent unauthorized activities. Moreover, auditing mechanisms should be established to monitor key usage effectively, thus allowing for timely detection of any anomalies.
5. Key Rotation
To mitigate the risks associated with key compromise, key rotation is a best practice that involves the periodic replacement of cryptographic keys. Over time, keys may become vulnerable due to advances in computational capabilities or potential exposure through operational lapses. By regularly changing keys, organizations reduce the window of opportunity for attackers. However, key rotation must be carefully managed, as it can introduce complexities regarding continuity and operational disruptions.
6. Key Revocation
Despite rigorous preventive measures, there may be instances where keys need to be revoked. This can arise from various scenarios, including the loss of a private key, compromise of key integrity, or dissolution of the relationship with the key owner. Revocation mechanisms, such as Certificate Revocation Lists (CRLs) or the Online Certificate Status Protocol (OCSP), facilitate the timely invalidation of compromised keys, thereby protecting systems reliant on those keys from misuse.
Challenges in Key Management
While key management is essential for the secure operation of public key cryptography, it is not without challenges. The complexity of managing keys across multiple systems, platforms, and users can lead to inconsistencies and errors. Furthermore, the human factor remains a significant vulnerability, as social engineering attacks may result in unauthorized access to sensitive keys. Therefore, organizations must invest in comprehensive training and awareness programs to bolster internal security against human-centric threats.
Additionally, the evolving landscape of cryptography introduces challenges regarding compliance and regulatory requirements. The rise of quantum computing prompts concerns about the long-term viability of existing cryptographic algorithms, necessitating advancements in key management practices and the adoption of quantum-resistant methods.
Conclusion
Key management is a foundational pillar supporting the security framework of public key cryptography. Its multifaceted nature necessitates diligent attention and continuous improvement to address emerging threats and challenges. By implementing robust practices for key generation, distribution, storage, usage, rotation, and revocation, organizations can fortify their defenses and ensure the integrity of their cryptographic operations. As technology continues to evolve, so too must the strategies that govern key management, reflecting the dynamic interplay between security and innovation.






Leave a Comment