In the digital age, the transmission of messages has evolved into a sophisticated process, employing various methodologies of encryption to safeguard information. The mechanisms behind sending a message and ensuring its security encompass a range of technologies and practices. Understanding what happens when you send a message and the encryption that underpins it is crucial for comprehending the complexities of modern communication.
When a message is dispatched, it embarks on a journey that may seem instantaneous from the user’s perspective, yet it is fraught with intricate steps requiring careful management. The first stage in this process is the creation of the message. This might be a simple text note or a comprehensive multimedia presentation. Regardless of its form, the content must first be encapsulated within an appropriate protocol that governs how data is packaged and transmitted over the internet.
At the core of this transmission lies encryption, a process that serves as a guardian for sensitive information. Encryption algorithms transform readable data into an encoded format, rendering it indecipherable to unauthorized parties. There are many types of encryption methods employed during this phase, including symmetric encryption, asymmetric encryption, and hashing. Each of these methods has its own unique characteristics and applications.
Symmetric encryption is one of the oldest and most straightforward forms of encryption, wherein the same key is utilized to both encrypt and decrypt the message. This requires the sender and the recipient to share a common key, which poses challenges regarding key distribution and management. If the key is intercepted or compromised, the entire communication becomes vulnerable. Despite its simplicity, symmetric encryption remains a staple due to its speed and efficiency, particularly for large volumes of data.
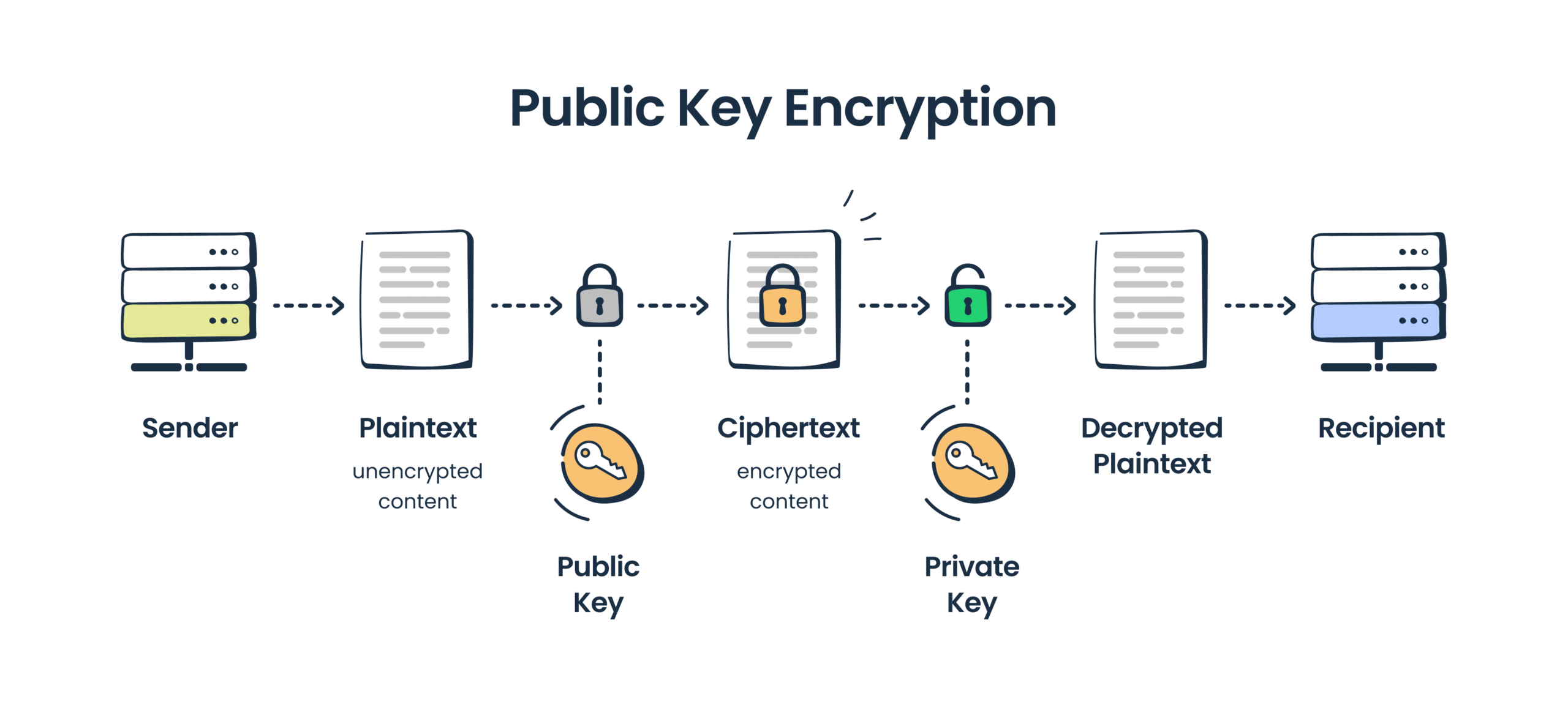
In contrast, asymmetric encryption introduces the concept of a key pair: a public key and a private key. The public key is disseminated openly, while the private key is kept secret by the recipient. When a sender encrypts a message using the recipient’s public key, only the corresponding private key can decrypt it, ensuring a high level of security during transmission. This technology is foundational to protocols like SSL/TLS, which secure internet interactions, protecting data exchanged in online transactions, social media interactions, and email communications.
Another critical aspect of encryption is hashing, which transforms data into a fixed-size string of characters, commonly expressed in hexadecimal format. Unlike encryption, hashing is a one-way function: it cannot be reversed to retrieve the original data. Hashing is frequently utilized to verify message integrity. For instance, when a message is sent, a hash of the message is created. Upon receipt, the recipient generates a hash of the received message to confirm that it remains unaltered during transit.
As messages traverse the vast expanse of the internet, they pass through numerous nodes and networks, each possessing its potential vulnerabilities. Each layer and site the message encounters poses distinct risks, such as interception or alteration. Therefore, implementing encryption techniques is essential for protecting against eavesdropping and ensuring the message’s confidentiality and integrity.
One contemporary communication protocol that exemplifies the modern application of encryption is Secure Socket Layer (SSL) or its successor, Transport Layer Security (TLS). These protocols imbue the exchange of information between web servers and clients with robust security mechanisms, ensuring that any data shared remains confidential and secure from prying eyes. When you click on a “secure” link indicated by HTTPS in your web browser, you are engaging with TLS, an encryption method that authenticates the communicating parties and protects the message content.
Furthermore, email encryption has become increasingly essential. Standard email protocols such as SMTP (Simple Mail Transfer Protocol) were not inherently designed with security in mind, necessitating the integration of encryption standards like PGP (Pretty Good Privacy) and S/MIME (Secure/Multipurpose Internet Mail Extensions). These protocols enable end-to-end encryption for emails, ensuring that only the intended recipient with the correct decryption key can access the message content.
Despite the advances in encryption technology, users must remain vigilant and well-informed about the potential pitfalls of digital communication. Phishing attacks and social engineering often exploit human behavior rather than technological vulnerabilities. Educating users on recognizing dubious emails and suspicious links is paramount in maintaining a secure communication environment.
Moreover, the rise of quantum computing threatens to revolutionize the encryption landscape, potentially rendering current cryptographic methods obsolete. Researchers are actively exploring post-quantum cryptography, which aims to develop new algorithms resistant to quantum attacks. This ongoing endeavor illustrates the dynamic nature of encryption and its perpetual evolution in response to emerging technological challenges.
To conclude, when a message is sent in our interconnected world, it encapsulates a wealth of processes, from encoding and encryption to transmission and security checks. The types of encryption employed in this journey, whether symmetric, asymmetric, or hashing, offer a myriad of safeguarding mechanisms. As individuals continue to exchange information across digital platforms, understanding these principles is imperative not only for the security of individual communications but also for the integrity of our increasingly digital society.






Leave a Comment