The intricate world of cryptography often feels like a labyrinthine maze. Among its many facets, one of the most critical and intriguing questions arises: How do you get someone’s public key? At first glance, the answer might seem straightforward, but as you delve deeper into the mechanics, an intricate tapestry of protocols, methods, and challenges unfolds. So, what if you were tasked with obtaining a public key from an acquaintance? Would you graciously ask them in person, or does the digital realm provide more innovative approaches? This inquiry may provoke a myriad of considerations encompassing trust, technology, and security.
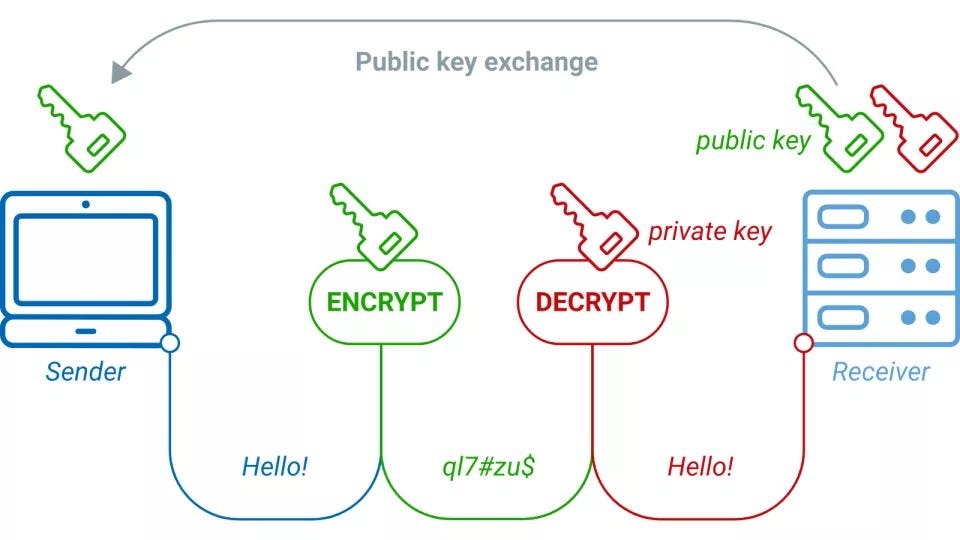
To elucidate the process of acquiring a public key, it is essential to first comprehend its role in the realm of asymmetric cryptography. Public keys operate on the premise of duality — each user has a unique pair of keys: a public key, which can be freely shared, and a private key, which remains confidential. The public key serves as a gateway for others to send encrypted messages that only the owner of the corresponding private key can decipher. This dynamic raises an intriguing challenge — how does one ensure the authenticity of a public key without falling victim to a fraudulent copy? Trust is an inherent component that forms the crux of public key distribution.
Consider the conventional method of direct exchange. In a face-to-face scenario, it is relatively straightforward to ask for a public key. For instance, a developer might hand over their public key to a colleague during a coffee break. However, even this seemingly innocuous act is rife with potential pitfalls. Is the person genuinely who they claim to be? This scenario emphasizes the necessity of trust; without it, the recipient may unknowingly accept a malicious public key, leading to significant security breaches.
In cases where direct interaction is not feasible, digital platforms often come into play. Email is a common method to transmit public keys. However, one must exercise caution; emails can be intercepted or manipulated, leaving recipients vulnerable. This necessitates the implementation of additional layers of verification. Digital signatures can play a pivotal role in establishing authenticity. By employing a trusted certificate authority (CA), an individual can sign their public key, creating a safety net that assures the recipient of its validity. But, if you’re relying on a CA, how do you confirm their trustworthiness? The answer lies in a complex web of trust models, each with its advantages and disadvantages.
Expanding on this notion of digital trust, one encounters the concept of the Web of Trust (WoT) used in systems like PGP (Pretty Good Privacy). In this decentralized framework, users validate each other’s public keys through direct interactions, thus creating a network of trust. By either endorsing keys or rejecting them, individuals build a community where legitimacy is established through personal connections. While this model encourages a kinship among users, it can create challenges in scalability. How do you manage trust when your network expands to hundreds, or even thousands, of participants? As connections proliferate, so too does the potential for miscommunication and mistrust.
Moreover, technological advancements have birthed innovative solutions like key servers and distributed ledgers, such as those utilized in blockchain technology. Key servers act as repositories, allowing individuals to upload and retrieve public keys while offering a layer of verification through community consensus. Yet, these systems are not without their foibles. To what extent do users rely on these servers? Is there a possibility that key servers may be compromised or become obsolete? These questions linger as cryptography continually evolves.
Now, let us delve deeper into the mechanics of public key acquisition process. For instance, an individual might utilize a QR code representation of their public key. By scanning the code, a user can quickly obtain the public key without entering it manually, eliminating the risk of typographical errors. However, what if the QR code has been tampered with? While innovative, this method can introduce vulnerabilities requiring users to double-check the source of the QR code.
Another avenue involves social media platforms; they have become modern-day vehicles for key distribution. Developers often share their public keys on platforms like GitHub, allowing potential collaborators to access them promptly. Nonetheless, this method lacks a significant layer of control over who can view or use these keys. It’s an open invitation — but to whom, and for what purpose? An air of uncertainty surrounds this mode of key sharing, amplifying concerns regarding privacy and potential misuse.
As we navigate through these intricate pathways of key acquisition, it is evident that the act of obtaining someone’s public key is far from straightforward. Each method presents its unique set of challenges and potential vulnerabilities, emphasizing the critical need for vigilance in this space. A playful yet pertinent question arises: What steps can one take to safeguard their communications when cryptography itself is constantly evolving? Analyzing each method’s risks and rewards ensures informed decisions that reflect the broader implications of digital interactions.
Ultimately, the journey to obtaining a public key encapsulates more than just technical prowess; it embodies a commitment to fostering trust and ensuring security in a digital landscape rife with uncertainty. As cryptographers and enthusiasts alike strive to fortify these channels of communication, continuous innovation and collaboration will lay the groundwork for a more secure future. Balance remains key in this endeavor, as each tool we employ can either serve as a bulwark against intrusions or a potential conduit for compromise.






Leave a Comment