In an era where data is the lifeblood of all digital interactions, safeguarding it during transmission has become paramount. The crux of the matter revolves around understanding how encryption can serve as a bulwark against potential breaches and intrusions. As digital landscapes evolve, so too do the methodologies employed by cybercriminals, both sophisticated and rudimentary. Consequently, the question arises: can encryption truly keep your data safe in transit?
To delve into this query, it is essential first to understand the nature of data itself. Data in transit refers to information actively moving from one location to another, such as across the internet or through a local network. Conversely, data at rest signifies inactive data stored physically in any digital form (like databases or data warehouses). The distinction between these two states must be acknowledged, for it shapes the approaches to their security.
Encryption is the process of converting plaintext into ciphertext, rendering it unreadable to unauthorized entities. The allure of encryption lies in its promise to protect data from interception during transmission. Various encryption protocols, such as SSL/TLS for web traffic and VPNs for secure remote access, exemplify tools employed to this end. Each method purports to create a virtual fortress around sensitive information while it traverses potentially perilous digital pathways.
Let us consider the efficacy of these protective measures. When data is encrypted, it becomes an insurmountable challenge for intercepting parties to decipher its content without the corresponding decryption key. This foundational principle undergirds the security of online transactions, including e-commerce activities and confidential communications. However, the robustness of encryption is often susceptible to the implementation practices surrounding it. Weak passwords, outdated algorithms, or improper key management practices can significantly diminish the fortress’s strength.
A common misconception is that data is impervious to breaches once encrypted. In truth, encryption is but one layer of a multi-faceted security strategy that ought to encompass vigilant cyber hygiene. While encryption serves as a formidable barrier against many forms of cyber threats, it is not an all-encompassing panacea. After all, if the endpoint security is compromised, the data can still be exposed before it is encrypted or after it is decrypted.
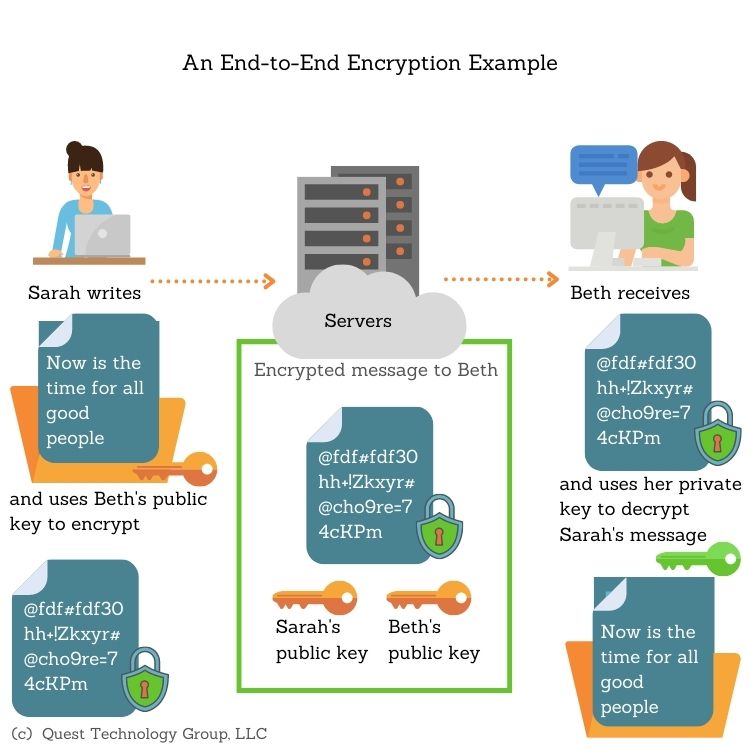
Moreover, it is worth examining the types of encryption available. Symmetric encryption employs a single key for both encryption and decryption, demanding that both communicating parties share the key securely. In contrast, asymmetric encryption uses a pair of keys—one public and one private—fostering a more flexible exchange. Each method possesses its advantages and limitations, and the applicability often depends on the specific context in which it is deployed.
The cryptographic algorithms themselves merit scrutiny. Advanced Encryption Standard (AES) and Rivest Cipher (RC4) are frequently deployed variants, yet their strengths can be undermined by cutting-edge computing capabilities and brute-force attacks. Thus, as the landscape of technology progresses, so too must the methodologies utilized for encryption adapt accordingly. This adaptability is crucial for maintaining data integrity.
A paradigm shift is further necessitated by the advent of quantum computing—an emerging frontier that threatens the very fabric of conventional encryption methods. The potential for quantum algorithms to unravel current encryption standards poses a significant existential threat. Consequently, researchers are racing to formulate post-quantum cryptography techniques capable of resisting such capabilities and ensuring continuity of robust data security.
As organizations grapple with these evolving threats, regulatory standards play an instrumental role in shaping practices surrounding encryption. Compliance mandates, such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA), compel entities to enact stringent data protection measures. Encryption often becomes a focal point in this dialogue, serving not only as a deterrent against breaches but also as a compliance fulcrum through which organizations can offer assurances regarding data stewardship.
However, the responsibility does not solely rest upon technology providers or regulatory bodies. Individuals also bear a critical onus in the encryption equation. Understanding the importance of robust password management, regularly updating encryption keys, and recognizing phishing attempts are all integral components of a comprehensive security posture. Furthermore, awareness around the software and services being utilized is essential; not all encryption solutions are created equal, and some may not provide adequate protection against contemporary threats.
To engender a systemic approach to encryption, communication is key. Organizations must foster a culture of security, encouraging employees and clients alike to recognize the imperative nature of safeguarding information in transit. User education can engender a sense of agency among individuals, transforming passive participants into vigilant defenders of data integrity.
The future of data transmission security rests on a dynamic interplay between encryption practices and evolving technological landscapes. While encryption serves as an essential tool, it is imperative to remain aware of its limitations and remain committed to continuous improvement in security methodologies. As we navigate this intricate digital terrain, the inquiry remains: can encryption keep your data safe in transit? The answer lies not only in the strength of the encryption itself but in the collective efforts of individuals, organizations, and technology to forge a more secure, vigilant approach to data safety and integrity.








Leave a Comment