The digital landscape has transformed significantly over the past few decades, and at the heart of this evolution lies an intricate web of protocols and standards designed to secure the online experience. Among these, Secure Sockets Layer (SSL), Transport Layer Security (TLS), and Hypertext Transfer Protocol Secure (HTTPS) are often referenced, yet the nuances that separate them frequently lead to confusion. This article endeavors to elucidate these technologies, their functions, and their significance in fostering a secure digital environment.
The Security Framework: An Introduction
Understanding SSL, TLS, and HTTPS requires a foundational grasp of their roles in web security. SSL was the original protocol developed by Netscape in the mid-1990s to establish secure connections over the internet. However, as vulnerabilities were discovered, SSL evolved into TLS, which is now the primary protocol employed for secure communication. While the terms are often used interchangeably, it is essential to recognize that TLS has superseded SSL.
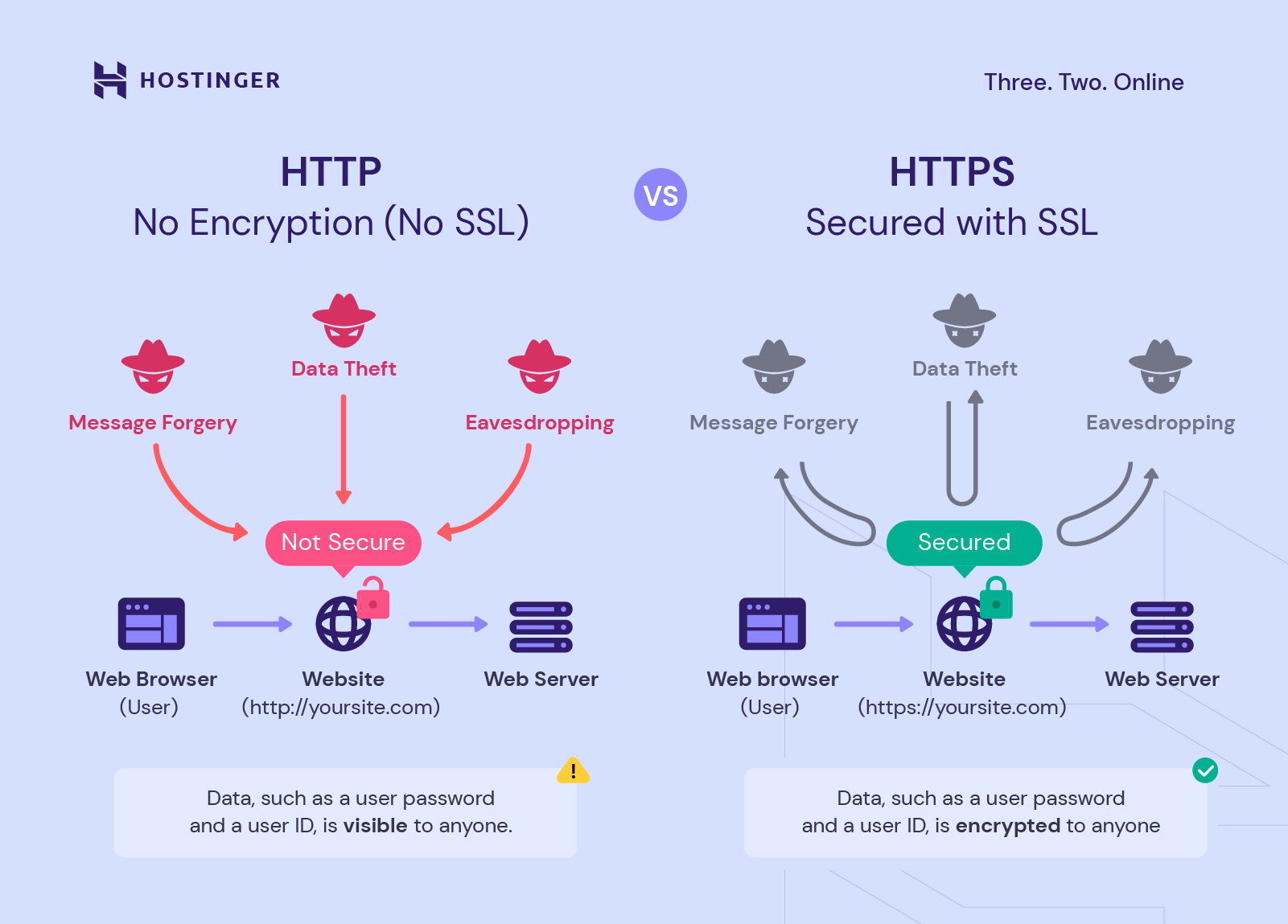
HTTPS, on the other hand, is not a protocol in itself but rather an extension of HTTP that utilizes SSL/TLS to encrypt data transmitted between a user’s browser and the web server. This encryption ensures that sensitive information, such as personal data and payment details, remains confidential and protected against eavesdroppers and attackers.
SSL and TLS: The Mechanics of Encryption
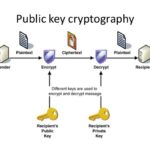
The crux of both SSL and TLS lies in their ability to encrypt data streams. The encryption process initiates when the client (usually a web browser) requests a secure connection from the server. This triggers a handshake process—a metaphorical handshake between the two parties—where they exchange cryptographic keys and negotiate the parameters of the secure session.
During the handshake, the server presents its digital certificate to the client, which contains the server’s public key. This certificate, typically issued by a trusted Certificate Authority (CA), serves as proof of the server’s identity. Upon verification, the client encrypts a random symmetric session key with the server’s public key and sends it back. The server decrypts this message using its private key and establishes a secure communication channel. The use of symmetric encryption during this session not only enhances efficiency but also ensures robust security.
In summary, TLS strengthens the original SSL framework. It provides enhancements such as better security algorithms, improved performance, and vulnerability fixes. Hence, distinguishing between archival reference to SSL and contemporary usage of TLS is crucial when discussing web security.
HTTPS: The Secure Communication Channel
Incorporating TLS into HTTP yields HTTPS, a protocol essential for secure online browsing. The significance of HTTPS extends beyond mere encryption; it also encompasses authentication and data integrity. By encrypting sensitive information such as passwords and credit card numbers, HTTPS mitigates the risk of man-in-the-middle attacks, in which intruders intercept and potentially manipulate data exchanges.
Moreover, modern web standards, influenced by search engines and user expectations, favor HTTPS over HTTP. Websites employing HTTPS are often ranked higher in search results, as search engines prioritize secure sites to ensure user safety. This shift mandates that organizations contemplate not merely the security of transmissions but also the competitive edge that comes with adopting HTTPS.
Types of Certificates: Varieties of Trust
The trustworthiness of HTTPS largely depends on the types of digital certificates obtained from Certificate Authorities. These certificates may be categorized based on the validation procedures they undergo:
- Domain Validated (DV) Certificates: These certificates provide basic encryption with minimal validation. The CA verifies that the applicant controls the domain, making them suitable for small sites with lower security needs.
- Organization Validated (OV) Certificates: These undergo a more thorough validation process, requiring verification of the organization’s identity. This type is more appropriate for businesses that wish to establish greater trust with their users.
- Extended Validation (EV) Certificates: The most rigorous form of validation, EV certificates involve extensive checks of the organization’s legal, physical, and operational existence. Browsers display a green address bar for sites using EV certificates, offering users a visible cue of safety.
Organizations must carefully select the appropriate certificate for their needs, as the level of trust communicated to users varies significantly between certificate types.
The Importance of Keeping Up with Standards
The realm of web security is perpetually evolving. As new threats emerge, protocols like TLS undergo revisions to address vulnerabilities. Consequently, staying abreast of updates—such as the transition from TLS 1.0 and 1.1 to TLS 1.2 and 1.3—is paramount. These newer versions feature enhanced security mechanisms, including improved performance metrics and stronger encryption algorithms that contribute significantly to a secure online environment.
Moreover, organizations must mandate periodic reviews of their security certificates and configurations. This diligence ensures that not only do they comply with the latest security standards, but they also reinforce the trust of their users.
Conclusion: The Imperative of Secure Connections
In an age where cyber threats abound, understanding the intricacies of SSL, TLS, and HTTPS is pivotal. The secure exchange of information transcends mere encryption; it embodies a holistic approach towards protecting user trust and securing digital interactions. With the ever-increasing reliance on online platforms for sensitive transactions, organizations must prioritize robust security protocols. Fostering a secure web environment is not just a technical necessity but a fundamental responsibility towards users.






Leave a Comment