Encryption keys serve as the backbone of cryptographic systems, enabling secure communication and data exchange in an increasingly digital world. This article elucidates the multifaceted processes involved in the generation, storage, and sharing of encryption keys, illuminating various methodologies and practices adhered to by cryptography experts.
Key Generation
Key generation is a crucial step in cryptography, determining the strength and security of the encryption mechanism. There are two principal methods for generating encryption keys: deterministic algorithms and non-deterministic processes.
Deterministic algorithms, such as those based on mathematical formulas or pseudorandom number generators (PRNGs), yield keys that can be reproduced if the initial conditions are known. Here, the randomness quality relies heavily on the entropy source provided to the algorithm. This method is prevalent in symmetric key algorithms, where identical keys are utilized for both encryption and decryption.
In contrast, non-deterministic processes harness unpredictable phenomena to generate keys. Events such as system timings, user interactions, or environmental noise can act as entropy sources, producing truly random keys. Non-deterministic key generation is critical for asymmetric cryptographic systems, where pairs of keys (public and private) are generated such that the public key does not reveal the private key. This method enhances security by making it computationally infeasible to derive the private key from the public key.
The complexity of key generation requires careful analysis of the key length, as longer keys typically offer increased security. Standard practices often recommend key lengths of at least 256 bits for symmetric encryption and 2048 bits or more for asymmetric encryption to mitigate the risk of brute-force attacks.
Key Storage
Once generated, the secure storage of encryption keys is paramount to safeguarding sensitive information. Keys can be stored in various repositories, each with its advantages and vulnerabilities. Common storage solutions include hardware security modules (HSMs), key management software, and secure cloud services.
Hardware Security Modules are dedicated physical devices specifically designed for safe key storage and management. They provide robust security against physical tampering and unauthorized access through mechanisms like encryption, access controls, and audit logs. While HSMs offer unmatched security, their deployment can be costly, making them more suitable for organizations handling significant volumes of sensitive operations.
Alternatively, key management software provides a flexible solution for key generation and storage, typically supporting various encryption standards. These applications utilize encryption protocols to protect the keys while in storage. However, their security hinges on the robustness of the software and the underlying infrastructure, making them a bit more susceptible to cyber threats.
Secure cloud storage has emerged as a popular method for managing encryption keys, particularly for organizations transitioning to cloud services. Storing keys in the cloud can enhance accessibility and reduce infrastructural burden. However, this method also introduces potential risks, including dependence on third-party security practices and concerns regarding data sovereignty.
Regardless of the storage method utilized, adopting practices such as regular key rotation, access control policies, and biometric authentications is vital in minimizing risks associated with key management.
Key Sharing
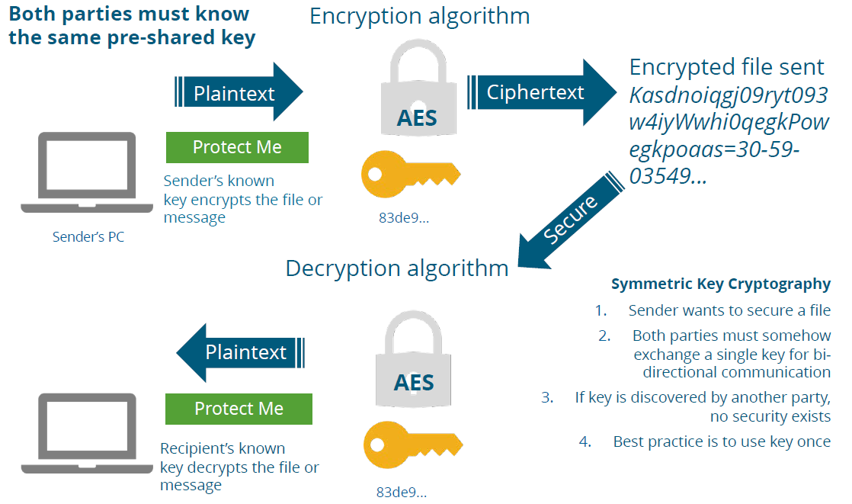
Sharing encryption keys securely is critical for maintaining the confidentiality and integrity of encrypted data. Key sharing can occur through several methods, with varying degrees of complexity and safety. One common approach is through asymmetric encryption, where the sender encrypts the key with the receiver’s public key. As the public key does not disclose the corresponding private key, only the intended recipient is capable of decrypting the shared key, ensuring its confidentiality during transmission.
Another avenue for key exchange is through secure channels, such as secure sockets layer (SSL) or transport layer security (TLS). These protocols establish an encrypted communication pathway, allowing for keys to be transmitted safely over the Internet or insecure networks. The utilization of ephemeral keys—temporary encryption keys generated for a single session—can further enhance security, reducing the risk of keys being reused or intercepted.
It is also essential to employ key exchange protocols like Diffie-Hellman, which enable two parties to establish a shared secret over an insecure channel. This process relies on the mathematical difficulty of solving discrete logarithms, thereby providing a reliable complement to the encryption ecosystem.
However, while advanced methods enhance security, they also introduce complexity, potentially creating pitfalls for those unfamiliar with their implementation. Organizations must strike a balance between security and usability, often necessitating training or simplified methods of secure key sharing.
Conclusion
Encryption keys are the linchpin of modern cryptographic systems, influencing the security landscape across diverse sectors. Effective key generation, storage, and sharing practices are critical for protecting sensitive information from prying eyes. As technology evolves, embracing sophisticated methodologies while maintaining user accessibility will be imperative in securing data against the increasingly intricate threat environment. Understanding the underpinnings of encryption key management is thus essential for anyone seeking to navigate the complexities of digital data security.








Leave a Comment