In the digital landscape of the modern age, the concept of security has taken on unprecedented significance. Each time you connect to a website, share sensitive information, or conduct an online transaction, there is an unseen yet highly sophisticated mechanism at play – the use of cipher suites. These codebooks play an integral role in safeguarding your data, creating a secure tunnel through which sensitive information can traverse safely. But what exactly is a cipher suite, and how does it facilitate secure connections in our daily online interactions?
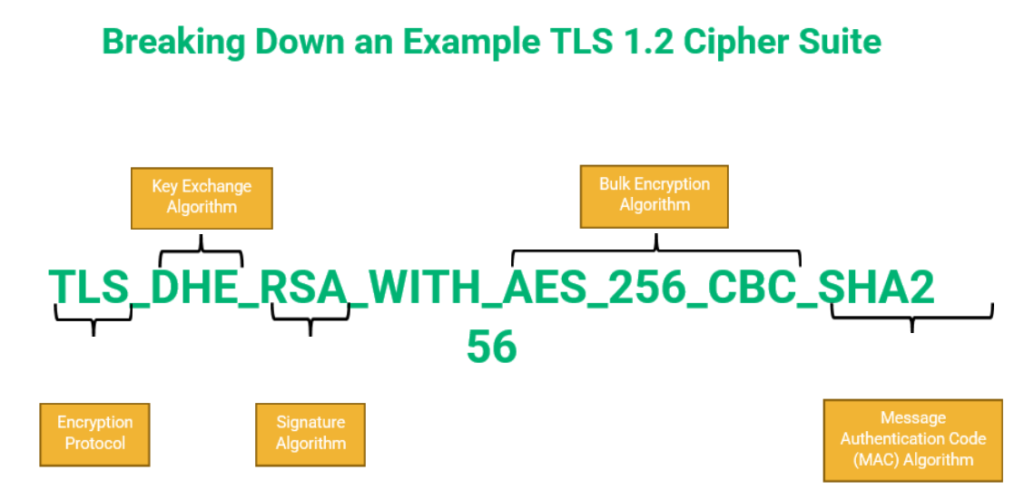
A cipher suite is, at its core, a set of cryptographic algorithms that dictate how data is encrypted and decrypted during transmission. Each suite consists of a combination of key exchange algorithms, authentication protocols, and message authentication codes (MACs). This trifecta works in concert to ensure that your data remains confidential and intact while traversing potentially treacherous networks, such as the internet.
One common observation is that users often take for granted the ease with which they can access their online banking or shopping accounts. It is easy to overlook the foundational technology that provides this remarkable level of security. Recognizing the role of cipher suites illuminates a deeper fascination with the intricacies of online safety and the techniques employed to thwart nefarious actors. To comprehend this better, it is essential to delve into the components that make up these cipher suites and how they function in real time to protect your data.
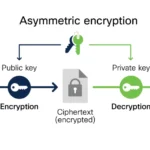
Consider the key exchange algorithms first. These algorithms are critical as they establish a secure method by which two parties can share encryption keys without eavesdroppers deciphering them. Examples include the Diffie-Hellman and Elliptic Curve Diffie-Hellman protocols. Such algorithms create ephemeral keys that are not found in any databases, meaning even if intercepted, they are virtually useless.
Next is the authentication process, which ensures that the entities involved in the communication are who they claim to be. Without authentication, any malicious actor could impersonate a legitimate website, leading to what is known as Man-in-the-Middle (MitM) attacks. By employing proven mechanisms such as RSA or Digital Signature Algorithm (DSA), systems can validate the identity of communicating parties, establishing a strong foundation upon which secure communications can be built. One must appreciate the significance of trust within digital interactions which cipher suites inherently foster.
Finally, the message authentication codes serve a pivotal role in maintaining the integrity of transmitted data. This last line of defense checks whether the information has been tampered with during transmission. MAC algorithms like HMAC (Hash-based Message Authentication Code) ensure that even if data is intercepted, it cannot be altered undetected. Such comprehensive protection is crucial, especially given the increasing instances of cybercrimes worldwide. The very architecture of our daily online experiences relies heavily on the unseen guardians provided by cipher suites.
One might ponder why this realm of encryption captivates many. The allure lies in the sheer complexity and effectiveness of the underlying mathematics that makes secure communications possible. Cipher suites are a fine illustration of how abstract mathematical concepts translate into practical, real-world applications. The usage of primes and elliptic curves, for instance, draws enthusiasts into the world of discrete mathematics and cryptography. This elegant blend of theory and practice not only provides security but also serves as a testament to human ingenuity and the relentless pursuit of privacy in a rapidly digitizing world.
The implementation of cipher suites is most visible when utilizing the HTTPS protocol, which secures data transferred between your browser and the websites you visit. A quick glance at the address bar reveals the presence of “https://” – a telltale sign of a secure connection. This ubiquitous usage has become an implicit expectation among users, further underscoring the societal shift towards prioritizing online security. However, the varying strength and sophistication of cipher suites means not all HTTPS implementations are created equal, leaving users vulnerable if they inadvertently connect to poorly configured servers.
The increasing complexity of required cipher suites also reveals some vulnerabilities. As vulnerabilities in cryptographies such as the widely deprecated SHA-1 hash function illustrate, not all systems can keep pace with the rapid evolution of computing power or cyber threats. This necessitates a continuous evolution in the cipher suites employed, underscoring the pressing need for not only understanding but also upgrading the very underpinnings of our digital interactions.
Moreover, the conversation around cipher suites opens pathways to several discussions about digital trust, privacy concerns, and regulatory policies. With the growing prevalence of secure connections, it is now critical to consider who has access to personal data, how it is stored, and what measures are in place to safeguard it. Balancing security with usability remains an ongoing challenge in our tech-driven existence, driven forward by advancements in cipher methodologies.
Ultimately, the fascination surrounding cipher suites is rooted in a blend of critical necessity and intellectual intrigue. The profound implications of these cryptographic structures influence not only the way we connect securely every day but also shape the broader landscape of digital ethics and rights. Engaging with this technology offers insight into the very heart of secure communications, serving as a pathway to ensuring a safer digital future for all users.
As we continue to explore the digital universes we inhabit, understanding the mechanics behind cipher suites will remain paramount. For every click, every transaction, and every communication, these cryptographic safeguards work relentlessly in the background, securing our digital interactions one connection at a time.




Leave a Comment