Cryptography, the art of concealing and revealing information, can often seem like a labyrinthine domain, accessible only to the mathematically inclined. However, an exploration into its fundamentals reveals a fascinating tapestry of security, secrecy, and communication. Imagine a mystical castle, where messages travel between towers. Each tower employs a unique mechanism to ensure that only the rightful owner can read the scrolls delivered within. This analogy serves as a doorway to understanding the purpose and mechanics of cryptography without delving into complex mathematics.
At its core, cryptography is akin to a sophisticated form of storytelling. Just as tales convey secrets among familiar companions, cryptography narrates messages intended exclusively for select audiences. The fundamental principle hinges on the transformation of readable information, also known as plaintext, into an inscrutable format termed ciphertext. This metamorphosis is facilitated through algorithms or ciphers—tools that perform these transformations—some of which have been designed over centuries, while others are products of contemporary advancements.
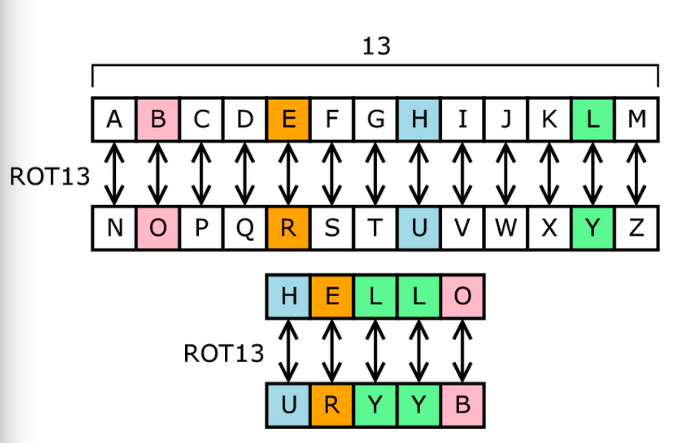
The journey begins with the simplest form of cryptography: substitutive ciphers. Imagine substituting characters in your favorite book with different symbols. A becomes @, B turns into 8, and so forth. This fundamental practice serves as a rudimentary shield against casual observation. While this method was sufficient in the bygone eras of handwritten correspondence, contemporary threats necessitate far more nuanced approaches.
As we usher in the modern era, public-key cryptography emerges, akin to a magical key that opens a mystical gateway. It employs a pair of keys—a public key, which everyone can access, and a private key, known solely to the user. Envision a mailbox that anyone can drop letters into, but only you possess the key to retrieve them. This unique symbiosis creates a secure channel for communication, even in a world brimming with potential eavesdroppers.
Furthermore, the concept of hashing resembles a culinary recipe. When you mix ingredients—flour, eggs, and sugar—you obtain a cake. However, you cannot revert the cake back to its original components. Hashing embodies this principle in the digital realm. A small chunk of data is input, and a fixed-length string is produced, representing that data. This abstraction is useful for confirming integrity, ensuring that even the slightest alteration transcends the original form.
The metaphor of a fortress provides a robust representation of cryptographic security. Just as a castle has battlements and moats to fend off intruders, cryptography employs various layers of protection to safeguard data. These layers include encryption algorithms, secure protocols, and extensive security practices. The strength of a cryptographic fortress lies not only in its physical structure but also in its strategy, adaptability, and continuous evolution in response to emerging threats.
Privacy and authentication are critical aspects of the fortress analogy. Imagine a medieval knight approaching the castle gates, invoking a secret passphrase to gain entry. Similarly, in the digital domain, authentication mechanisms verify identities, ensuring that users are who they claim to be. This authentication relies on elements such as passwords, biometric data, or multifactor authentication, forming an indispensable barrier against intruders.
With the intermingling of technology and society, blockchain technology arises as a revolutionary contribution to cryptography. Picture a ledger that everyone can view and verify, but modify only under consensus. Each transaction creates a link in a chain, ensuring transparency and security. The decentralized nature of blockchain diminishes the vulnerability associated with traditional databases, granting individuals greater control over their information.
The allure of cryptography extends beyond technical jargon; it evokes a sense of intrigue and creativity. Like an artist’s palette filled with colors waiting to be blended, cryptographic techniques empower individuals and organizations to craft their means of communication. From securing transactions to safeguarding sensitive information, cryptography evokes trust in an uncertain environment, bolstering the foundation of digital interactions.
Yet, beneath the surface of this enchanting realm lies a shadow—a dance of cat and mouse between cryptographers and adversaries. Just as one might devise a clever heist to infiltrate a fortified castle, malicious actors continuously innovate methods to bypass cryptographic defenses. The continuous arms race in this arena underscores the importance of ongoing research and development. Cryptographers are akin to skilled artisans, tirelessly refining their craft in pursuit of unbreakable codes.
In conclusion, cryptography may initially appear as an esoteric discipline shrouded in complexity, but it is fundamentally grounded in safeguarding communication and preserving privacy. Through captivating metaphors, one can visualize its intricate workings without becoming daunted by the mathematical underpinnings. The narratives of substitution, public-key systems, hashing, and blockchain all weave a compelling story of security, empowerment, and resilience. Understanding the essence of cryptography does not require advanced calculus or abstract algebra; it requires a curious mind and a willingness to explore the fascinating interplay of secrecy and transparency in our interconnected world.







Leave a Comment