The digital realm has transformed our methods of communication, documentation, and interaction. In this landscape, the importance of security and authenticity cannot be overstated. Just as a stamp of approval historically signified legitimacy on papyrus scrolls or parchment, digital signatures serve as modern-day bastions of trust in electronic documents. When it comes to the Portable Document Format, or PDF, a common query arises: Can digital signatures be appended to these ubiquitous files? To explore this question, a deeper understanding of the technology, standards, and implications is essential.
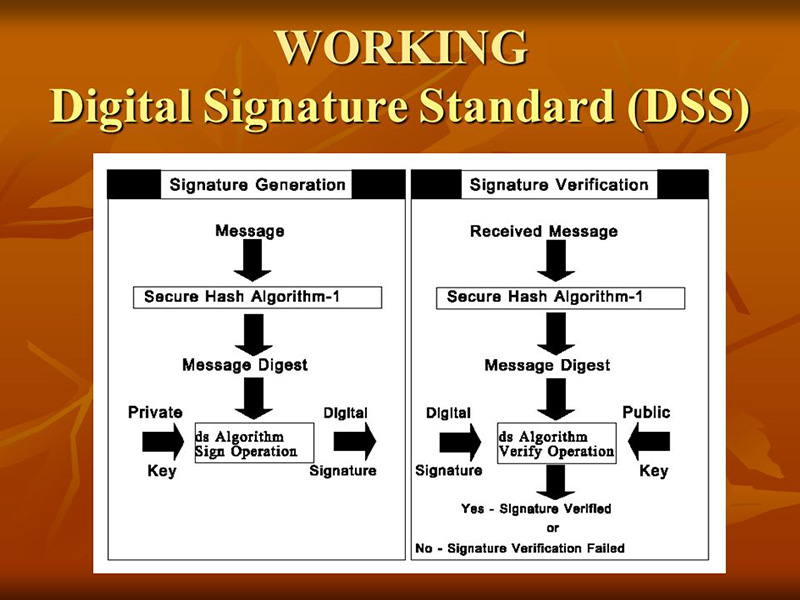
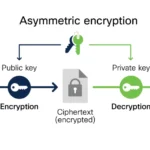
At the very heart of this inquiry lies the Digital Signature Algorithm (DSA) and the Digital Signature Standard (DSS). The DSA, an integral piece of cryptographic machinery, enables the verification of both the signer’s identity and the document’s integrity through the utilization of an asymmetric cryptographic system. Here, the metaphor of a locked treasure chest becomes apt: the document is locked, the signer’s private key serves as the key to the chest, while the public key acts as the means by which others can validate the contents without compromising their security.
Now, consider the PDF format itself. It’s a versatile and widely favored allocation for sharing static documents across platforms, preserving formatting regardless of device or operating system. However, the original PDF specification did not inherently incorporate the capability for digital signatures. This limitation rendered it akin to a beautiful painting, framed perfectly, yet lacking an inscription of authenticity that solidifies its provenance.
As technology advanced and the necessity for secure electronic signatures surged, the PDF specification evolved. With the introduction of PDF 1.5, the ability to embed digital signatures emerged, providing a much-needed antidote to the inconsistencies that plagued document authentication. This enhancement allowed for the creation of a secure signature field, analogous to a notary public who witnesses and verifies a transaction.
The digital signature process within a PDF involves several steps: the signer first creates a hash of the document, generating a unique fingerprint. Subsequently, this hash is encrypted with the signer’s private key, resulting in the digital signature. With the signed document now complete, it can be sent to the recipient, who can use the signer’s public key to decrypt and verify the signature. If the decrypted hash matches the document’s hash, authenticity is confirmed. Much like a hidden seal on a wax envelope, this process assures the recipient of the document’s integrity.
However, the PDF’s digital signature capabilities are not merely a technical curiosity. They are governed by protocols and standards that ensure uniformity and interoperability across different systems. The most prominent among these is the Public Key Infrastructure (PKI), which relies on a complex hierarchy of certificate authorities (CAs) to both issue and manage digital certificates. Think of this structure as a sprawling tree, with the root CA as its trunk, branching out into numerous subordinate CAs down to the leaves—individual signers. Each branch must remain healthy and authenticated to maintain the integrity of the entire system.
Additionally, the use of the PAdES (PDF Advanced Electronic Signatures) standard further solidifies the digital signature’s place within the PDF format. This standard addresses not only the creation of signatures ensuring their validity over time but also compliance with various legal frameworks around the world. It encapsulates the concept of longevity, similar to a well-preserved artifact in a museum that continues to tell its story generations later, rather than fading away into obscurity.
Yet, the landscape of digital signatures is not without its challenges. A significant concern revolves around the reliance on digital certificates issued by CAs. The security of the entire digital signature framework hinges on the trust placed in these entities. If a CA were to be compromised, it has the potential to undermine the authenticity of all signatures based upon that authority. Thus, stakeholders must remain vigilant, continually assessing and fortifying their trust frameworks.
Moreover, the technical knowledge required to implement digital signatures in PDFs can be a barrier for many individuals and organizations. The perception of complexity can deter users from embracing what is actually an invaluable tool for security. To mitigate this, user-friendly software solutions have emerged, transforming the process into a seamless experience, akin to flipping a switch in a dimly lit room to reveal the vibrant colors hidden within. This democratization of digital signatures invites broader adoption, fortifying the trust fundamental to digital transactions.
In terms of practical applications, the array of scenarios where digital signatures can be utilized is impressively diverse. Legal documents, contracts, financial statements, and even personal communications can benefit from this secure method of authentication. Imagine the ease with which a remote workforce can validate agreements without the need for physical signatures, narrowing the logistical chasm between disparate geographies.
Ultimately, as the digital landscape continues to expand and evolve, the question of whether digital signatures can be added to PDFs is surpassed by a more profound realization. The standards supporting these signatures are not merely technicalities; they are fundamental threads woven into the fabric of modern communication and trust. Digital signatures embody the assurance that, despite the ephemeral nature of the digital world, authenticity, integrity, and security can still reign supreme. In an era when deception looms large, the digital signature stands resolute—an emblem of trust piercing through the veil of uncertainty.




Leave a Comment