AES-GCM (Advanced Encryption Standard – Galois/Counter Mode) is a popular encryption algorithm heralded for its efficiency and security in authenticated encryption. A prevalent question surrounding this cryptographic technique pertains to whether AES-GCM requires padding, especially in instances where its use is critical in secure communications. To unravel this query, one must delve deep into the workings of AES-GCM, particularly in relation to data size, block size, and the nuances of padding.
At its core, AES operates on a block size of 128 bits, which corresponds to 16 bytes. For data lengths that do not naturally align with this block size, the challenge of alignment surfaces. This is where the concept of padding comes into play. Traditional block cipher modes—like CBC (Cipher Block Chaining)—depend on padding mechanisms to ensure that plaintext data conforms to the required block length. This is accomplished through various techniques, the most prominent being PKCS#7, which appends bytes reflecting the amount of padding added.
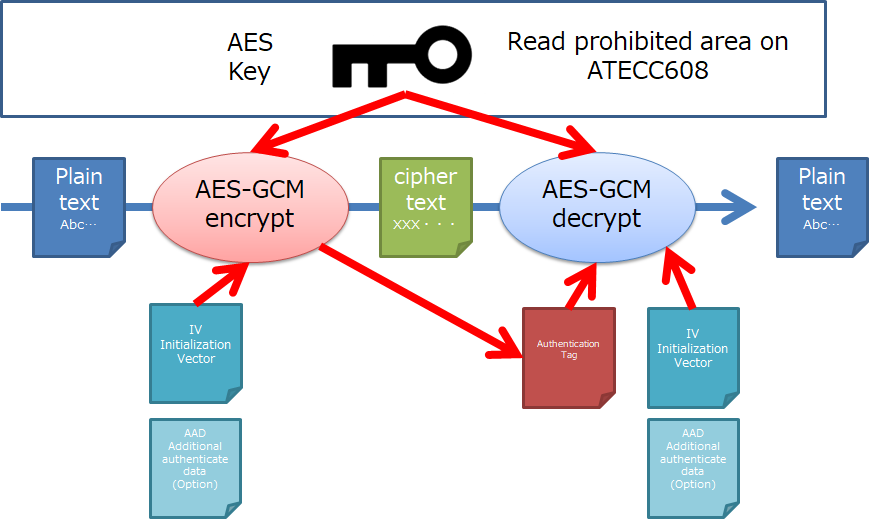
However, AES-GCM distinguishes itself from these classic modes, as it is fundamentally a stream cipher mode. The ingenious design of GCM allows it to encrypt data in a manner that can accommodate variable lengths without necessitating padding as a standard practice. The GCM mode processes blocks of plaintext independently, creating a seamless flow of data that negates the need for artificial extensions that padding introduces.
Yet, it is crucial to understand that while padding is not strictly required, this does not imply that the developer can disregard data length entirely. GCM requires the plaintext length to conform to specific parameters. One of the key characteristics of GCM is that it operates efficiently for data sizes that do not exceed multiples of 128 bits. Whereas if the data’s length is less than 128 bits, GCM can still function, but the encryption of these segments may present a unique challenge related to the nature of the security guarantees it provides.
This characteristic leads to a pivotal distinction: while AES-GCM does not require padding for the encryption process, the external handling of data sizes is essential. Developers must ensure that any message or data sent is well-structured. If padding is employed externally before encryption, it should not interfere with the integrity of the data at the point of encryption. Such external methodologies often lead to confusion, creating a misconception that padding is an inherent requirement of AES-GCM.
Furthermore, it is advantageous to consider security implications in adopting an encryption style like GCM without padding. The authentication mechanism built into GCM validates both plaintext and associated data, a feature that bolsters the security assurances provided by the algorithm. However, improper handling of data can lead to vulnerabilities or loss of the integrity checks that GCM provides. Thus, it becomes essential to integrate robust input validation and data handling procedures when implementing AES-GCM in practical applications.
The complexity of AES-GCM does not diminish when examining its operational aspects. The initial phases of the encryption process involve generating a nonce (number used once) that must be unique for each encryption operation. Coupled with an initialization vector (IV), this creates a unique context for encryption even when identical plaintext inputs are encrypted multiple times. This inherently addresses one of the classic concerns in cryptography: avoiding the reuse of keys and IVs, which could lead to catastrophic breakdowns in security.
Within this framework, a significant aspect remains the interaction between block sizes and message lengths. While GCM permits the encryption of variable-length data without padding, attention must be directed toward the output of such encryption processes. The lengths of the encrypted data must still correlate with anticipated operational parameters for successful decryption and integrity verification. Failure to observe this vital alignment could prompt vulnerabilities exploited by malicious actors.
Consequently, the operational landscape surrounding AES-GCM entails a balance between encryption, data size, and the appropriateness of padding. It is not only prudent to comprehend that AES-GCM does not require padding in a traditional sense. Rather, one must appreciate it as part of a broader cryptographic strategy that necessitates understanding how to manage plaintext lengths effectively while leveraging the powerful authentication features inherent to the mode.
In conclusion, the assertion that AES-GCM requires padding is a misconception rooted in a misunderstanding of the operational dynamics of this encryption mode. Instead, developers can navigate the complexities associated with data alignment and GCM’s requirements to fashion a secure encryption protocol that recognizes the unique benefits of AES-GCM. Equipped with this knowledge, security practitioners can effectively enhance the reliability and robustness of their cryptographic implementations.








Leave a Comment