The realm of cryptography is undergoing a metamorphosis, spurred primarily by the advent of quantum computing. As traditional cryptographic methods, such as RSA and ECC (Elliptic Curve Cryptography), become susceptible to the capabilities of quantum algorithms, the search for resilient cryptographic frameworks has intensified. Among the plethora of emerging alternatives, lattice-based cryptography has resurfaced as a formidable contender, eliciting interest from both academia and industry. Yet, amidst this burgeoning intrigue, a pertinent question arises: is anyone actually using lattice-based cryptography?
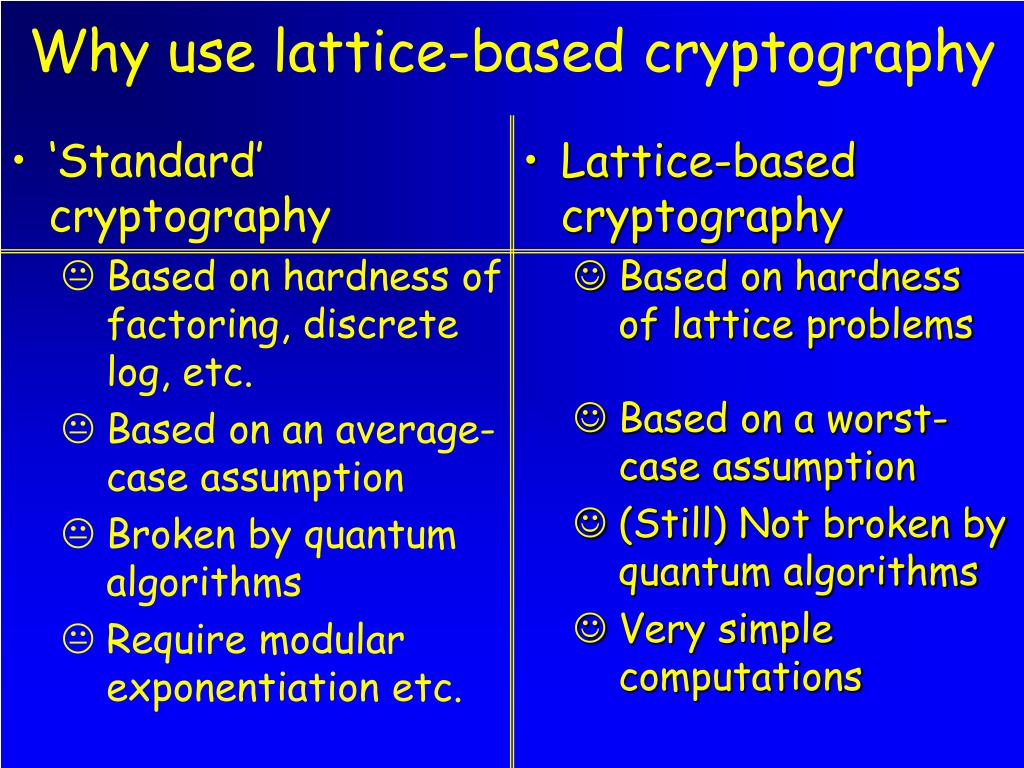
To address this query, it is crucial to dissect the inherent properties of lattice-based cryptography alongside its practical applications. Lattice-based cryptography is founded on the mathematical structure known as lattices, which are arrays of points in space that exhibit a periodic nature. The security of this cryptographic framework is predicated on the computational intractability of certain problems related to lattices, such as the Shortest Vector Problem (SVP) and the Learning With Errors (LWE) problem. Such hardness assumptions are conjectured to remain secure even in a post-quantum world, making them attractive to cryptographers.
As one delves into the realm of implementation, an ongoing discussion concerns the transition period from traditional to post-quantum cryptography. The National Institute of Standards and Technology (NIST) has embarked upon a rigorous standardization process for post-quantum cryptographic algorithms, which has garnered significant attention. Various lattice-based candidates are under review, including NTRU and FrodoKEM, both of which demonstrate promising features for practical deployment. However, the transition is far from seamless. Entities concerned with security must weigh the risks and benefits involved when moving from established protocols to novel solutions.
When examining current utilizations of lattice-based cryptography, it becomes evident that certain sectors are leading the charge. Financial institutions and governmental agencies, due to the cryptographic sensitivity of their operations, are vigilantly exploring lattice-based encryption methods. Several companies are conducting extensive pilot programs to analyze the efficacy of these methods. Notably, firms in the tech sector, such as Google and IBM, have engaged in research projects targeting the implementation of lattice-based schemes within their infrastructures, thereby instigating a gradual shift.
Further, lattice-based cryptography is not solely about encryption. It encompasses a broader palette of cryptographic primitives, such as digital signatures, homomorphic encryption, and zero-knowledge proofs. The versatility of these primitives has drawn the attention of researchers and practitioners alike. For example, the digital signature algorithm called “BLISS” (Bimodal Lattice Signature Scheme) derived from lattices, offers remarkable efficiency and security. The integration of such algorithms into existing systems could enable substantial enhancements in both speed and reliability, thereby compelling users to embrace this cryptography form.
An additional aspect worth discussing is the arena of hardware implementation. The performance of cryptographic protocols can significantly hinge on hardware capabilities. Notably, lattice-based cryptographic schemes often exhibit a more favorable performance profile on hardware platforms due to their inherent parallelizability. This manifests in reduced latency and increased throughput, particularly noteworthy for applications like secure communications and cloud services where speed is paramount. However, the requisite computational resources for such protocols are often higher than those traditionally utilized, necessitating ongoing advancements in hardware technology to facilitate widespread adoption.
Moreover, a substantial component of the lattice-based cryptography discourse pertains to education and awareness among developers and security professionals. As the cryptographic landscape evolves, a concerted effort to educate practitioners about these new paradigms is essential. Workshops, seminars, and academic courses focusing on lattice-based techniques are incrementally increasing, yet the material often remains esoteric. To truly harness the potential of lattice-based cryptography, the community must demystify these concepts, fostering broader understanding and familiarity.
Despite the considerable momentum gathered by lattice-based cryptography, several barriers to widespread adoption persist. Lack of robust libraries accessible for developers presents a critical challenge. While notable libraries such as NTRU and Lizard exist, they often lack comprehensive documentation and real-world usage examples. This absence of resources can dissuade developers from exploring their capabilities. Furthermore, as the ecosystem matures, collaborations among researchers and practitioners will inevitably prove vital in developing user-friendly libraries that facilitate the integration of lattice-based solutions into existing applications.
In conclusion, the inquiry regarding the practical usage of lattice-based cryptography reveals a nuanced landscape. Although tangible implementations are present, particularly in pioneering sectors, a full-fledged, pronounced adoption is still a work in progress. As cryptographic needs continue to evolve amid the quantum threat, the lattice-based paradigm stands poised at the forefront of innovation. The dual nature of its theoretical rigor and practical applicability underscores its potential viability. The journey toward universal adoption may be complex and fraught with challenges, yet the prospect of establishing a robust post-quantum cryptographic architecture renders it a worthwhile pursuit. As the cryptographic community forges ahead, one can anticipate a paradigm shift where lattice-based methodologies may one day offer the staple security we rely on in our digital lives.








Leave a Comment