Transport Layer Security (TLS) stands as the guardian of data privacy on the internet, a comprehensive protocol that ensures secure communications. In deciphering its operational fabric, a central question arises: Does TLS utilize symmetric or asymmetric encryption? The answer is both, as TLS employs a hybrid encryption model. This hybrid approach embodies the strengths of both encryption paradigms, fostering a secure yet efficient means of safeguarding digital interactions.
To truly appreciate the ingenuity behind TLS, one must first understand the basic tenets of symmetric and asymmetric encryption. Symmetric encryption employs a single key for both encryption and decryption processes. This means that both parties engaged in the communication must possess the same secret key, sharing it securely prior to the initiation of an encrypted session. The crux of symmetric encryption lies in its speed; it is typically faster than its asymmetric counterpart, making it suitable for encrypting large volumes of data.
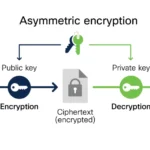
Asymmetric encryption, on the other hand, employs a pair of keys: a public key and a private key. The public key, as its name implies, can be shared openly, while the private key is kept secret. Data encrypted with the public key can only be decrypted with the corresponding private key, creating a secure channel for communication without the necessity of pre-sharing a secret key. The scalability and secure key exchange capabilities of asymmetric encryption make it an indispensable tool in modern cryptography.
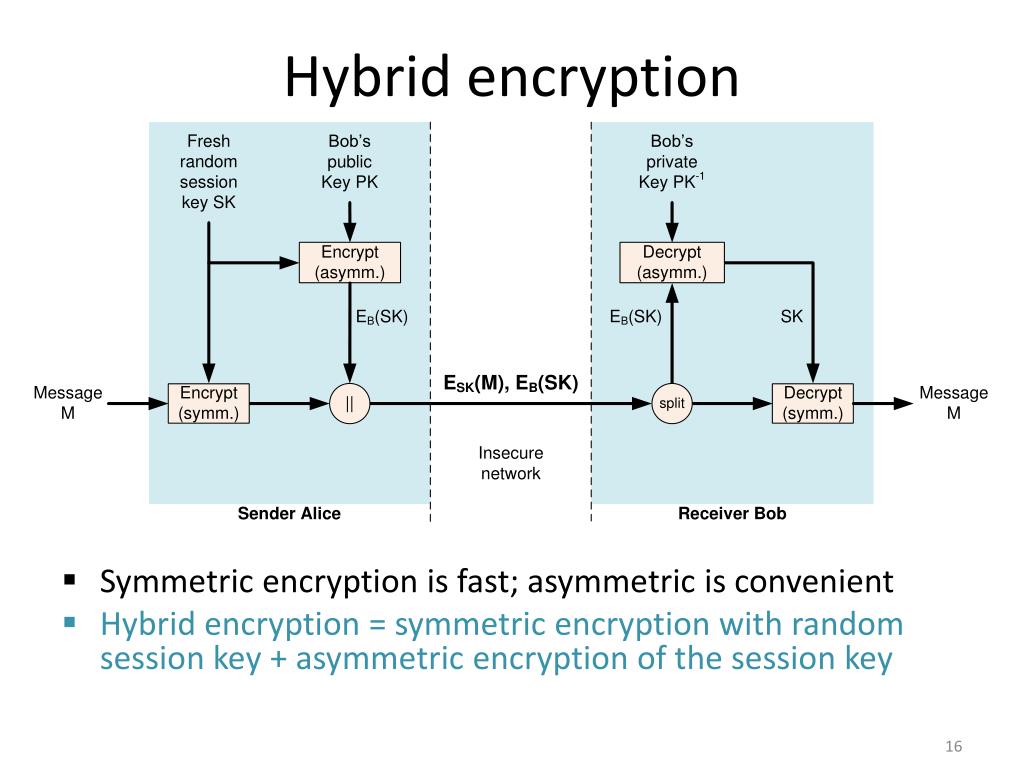
Understanding the coexistence of these methods within TLS reveals a system of layered security. When a client, such as a web browser, initiates a secure connection to a server, it first undergoes a handshake process, which serves as a cornerstone of the TLS protocol. During this handshake, asymmetric encryption plays a pivotal role. The server presents its public key, allowing the client to encrypt a randomly generated session key that only the server can decrypt with its private key. This exchange establishes a secure channel for the subsequent transfer of information.
Once the session key is securely established through asymmetric means, TLS shifts towards symmetric encryption for the actual data transfer. The session key, a short and unique random key, is employed to encrypt the communication between the client and server. This transition into symmetric encryption is largely due to its efficiency; the overhead associated with asymmetric encryption is substantially higher, making it less suitable for transferring large amounts of data over the sustained duration of a session.
The hybrid model utilized in TLS also presents intriguing implications for secure communications. By ingeniously combining both encryption types, it offers not only security but also enhanced performance. The initial use of asymmetric encryption provides robust security during the key exchange phase, ensuring that even if an adversary intercepted the transmitted keys, they would remain futile without the private key. The subsequent switch to symmetric encryption optimizes performance and allows for rapid data transfer, striking a delicate balance between speed and security.
Moreover, the reliance on a session key limits the exposure of symmetric keys throughout the communication. By generating a unique session key for each connection, TLS minimizes the risks associated with key compromise. Should a session key be uncovered, its applicability is limited to the session in question, thus deterring potential long-term repercussions. This aspect of discontinuity fundamentally enhances the resilience of the encryption framework.
Intriguing, however, are the computational nuances underpinning this hybrid approach. The overhead of asymmetric encryption demands substantial computational resources, leading to longer processing times compared to symmetric methods. This has prompted ongoing research into optimizing key exchange protocols and minimizing computation load. As computing power continues to evolve, the cryptographic community remains vigilant in adapting the mechanisms underpinning protocols like TLS, ensuring they remain robust against emerging threats.
Curiosity deepens when considering the range of applications for TLS. The usage of this hybrid model extends far beyond mere website security; it plays a pivotal role in safeguarding emails, securing instant messaging platforms, and fortifying foundational elements of the Internet of Things (IoT). With the growing imperative for secure data exchanges in an era of rampant cyber threats, understanding the intricacies of TLS is not merely an academic pursuit—it’s vital for every entity participating in the digital ecosystem.
As the digital landscape continues to burgeon, one must remain cognizant of the complexity surrounding encryption methods. The marriage of symmetric and asymmetric encryption within TLS epitomizes a sophisticated yet pragmatic approach to securing communications. It invites professionals and amateurs alike to reconsider their understanding of cybersecurity frameworks, encouraging an exploration of deeper implications and practices.
In conclusion, the multifaceted nature of TLS, with its reliance on both symmetric and asymmetric encryption, epitomizes how traditional cryptography principles can be reimagined to meet modern challenges. By harnessing the distinct advantages of both methods, TLS not only promises an effective shield against nefarious attacks but also unveils insights into the intricate dance of data security that governs our digital lives. Such an interplay deserves careful contemplation, particularly as one navigates the complexities of communication in the digital age.




Leave a Comment