In the intricate world of cryptography, block codes serve as foundational elements, akin to the building blocks of a grand edifice. These cryptographic constructs are pivotal for ensuring the confidentiality and integrity of messages communicated across insecure channels. As we delve into the nuances of block codes, one can liken them to the sturdy bricks used in constructing a fortress; each block serves its distinct purpose while contributing to the overall security structure.
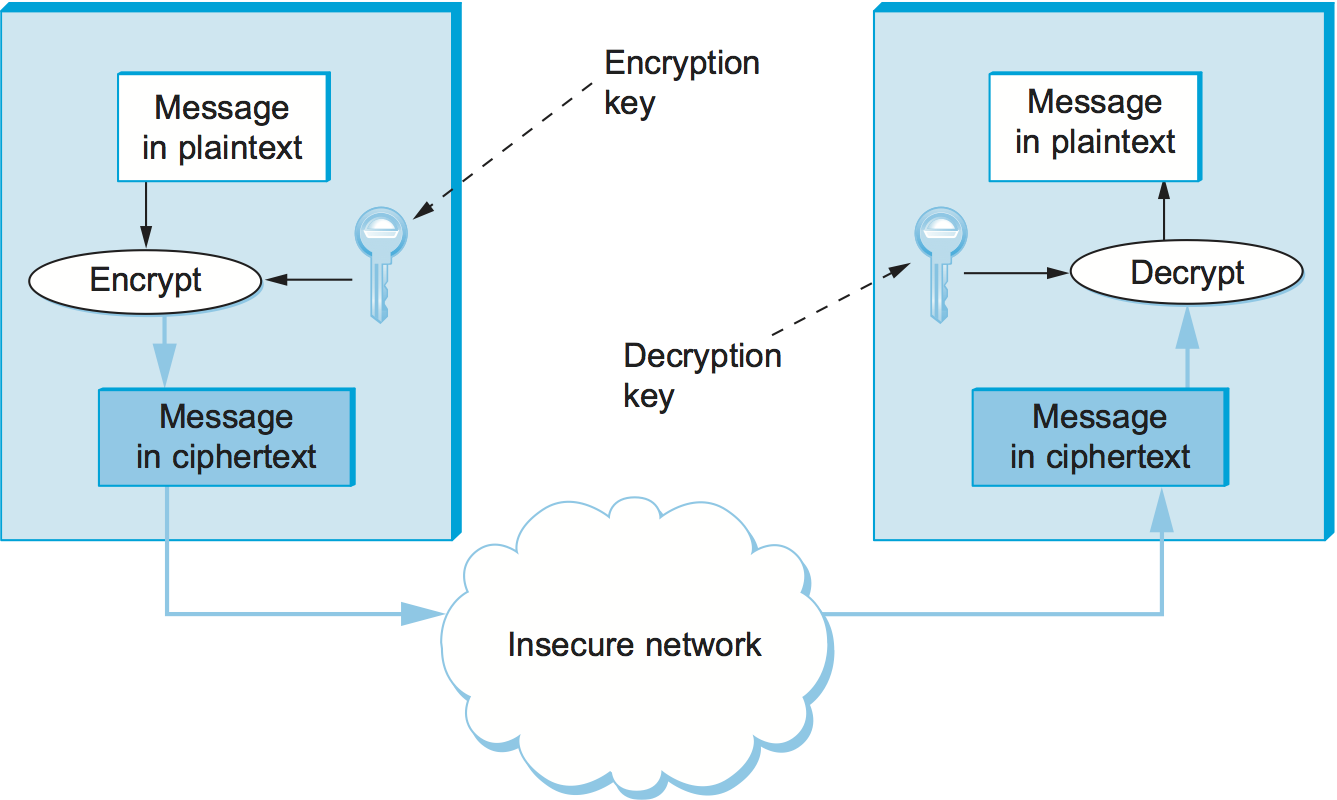
At the core of block coding lies the concept of fixed-size data units. Unlike other forms of cryptographic schemes that may operate on variable lengths, block codes process data in predefined chunks. The common practice involves transforming plaintext—human-readable information—into ciphertext via a systematic encoding process, where every block undergoes encryption to obscure its true meaning, thus preserving the confidentiality of the information encapsulated within.
To elucidate this process, consider a message parsed into blocks of a uniform size, commonly 64 or 128 bits. Each block is subsequently subjected to a transformation algorithm—often involving round functions that mix, substitute, and reorder bits—resulting in an encrypted output that bears no resemblance to its predecessor. This metamorphosis ensures a secure cradle for secrets, enveloping them in layers of complexity that can only be unraveled by those armed with the appropriate decryption keys.
The operational mechanics of block codes also revolve around various cryptographic principles, notably substitution-permutation networks (SPNs) and Feistel structures. SPNs utilize a combination of substitution—where bits are replaced according to a defined mapping—and permutation, which rearranges them, thus augmenting security through diffusion. Conversely, the Feistel structure opts for a more iterative approach, splitting each block in half and performing a sequence of transformations across the halves, significantly enhancing security while maintaining efficiency.
While discussing block codes entails technical terminology, it is imperative to understand their application and utility in real-world scenarios. A powerful metaphor comes to mind: consider the construction of a vault, meticulously designed to thwart unauthorized access. Each block code functions as a layer of this vault—every bolted segment an intricate puzzle piece, reinforcing the overall structure against infiltration attempts. With advancements in computational power, employing robust block codes has become paramount, leading to the development of advanced encryption standards (AES), which operates on 128-bit blocks with varying key sizes, commonly 128, 192, or 256 bits.
A vital characteristic of block codes is their ability to withstand various attacks. As adversaries grow more sophisticated, the necessity for formidable encryption becomes increasingly critical. Block codes mitigate various forms of cryptanalytic assault, including brute force attacks and differential cryptanalysis, each articulating the ongoing arms race between cryptographers and potential attackers. By employing techniques such as key strengthening and redundancy, block codes evolve, adapting to the burgeoning complexity of threats in the digital landscape.
In addition to security, block codes facilitate numerous applications that transcend mere confidentiality. They enhance data integrity, ensuring that any alterations to the encrypted message can be detected post-transmission. This self-verifying attribute resembles a hologram on a credit card; the integrity of the hologram serves as an assurance of authenticity, promising that the card has not been tampered with in transit. Consequently, cryptographers employ hash functions in tandem with block codes to authenticate messages, fortifying both message security and sender identity.
The relationship between block codes and error detection also merits exploration. In a world where data corruption can be as disastrous as eavesdropping, block codes emerge as champions in preserving fidelity against imperfections introduced during transmission. Utilizing redundancy in structured formats, they empower systems to identify and correct errors—a critical feature in high-stakes contexts such as banking and military communications, where the precision of information is non-negotiable.
Yet, block codes are not without their limitations. The rigid structure of fixed-length processing can lead to inefficiencies, particularly when dealing with variable-length data. Padding techniques must often be employed to accommodate shorter blocks, reminiscent of fitting an irregular item into a tidy box. As technology progresses, the quest for hybrid models that combine the strengths of block and stream ciphers continues. These approaches seek to merge the robustness of block encryption with the fluidity required for real-time data processing, heralding a new era of cryptography.
In conclusion, block codes represent an indispensable aspect of the cryptographic landscape, elucidating the intricate interplay between security, efficiency, and adaptability. They are the scaffolding upon which digital fortresses are built, embedding resilience against an array of threats while enabling the trustworthy transmission of information. As we navigate the complexities of a rapidly evolving digital society, the principles underlying block codes remain steadfast, offering a robust framework that safeguards our communications and nurtures our dependence on digital interactions.
Ultimately, as cryptography continues to evolve, the fundamental understanding of block codes remains a beacon; they illuminate the path toward secure messaging, solidifying their status as essential building blocks—resilient and ever-relevant in a cryptographic world rife with challenges.






Leave a Comment