Encryption is a cornerstone of modern digital security, providing confidentiality and integrity for sensitive information. Traditionally, encryption relies on keys—unique codes that transform plaintext into ciphertext. However, the notion of encrypting data without keys raises intriguing questions and challenges our conventional understanding of cryptography. This exploration into the realm of keyless encryption will reveal its complexities and ramifications.
To comprehend the feasibility of encrypting without keys, one must first delineate the distinctions between encryption and encoding. While both processes obscure information, encryption focuses on securing it for confidentiality purposes, necessitating decryption for retrieval. Conversely, encoding is about data representation rather than security and is inherently reversible without the need for secret keys. Thus, any viable discussion of keyless encryption must consider the foundational attributes of both approaches.
One alternative that has garnered attention is the concept of homomorphic encryption. Defined as a form of encryption that permits computations to be performed on ciphertexts, homomorphic encryption allows data to be manipulated while still encrypted, preserving privacy. Although traditional applications utilize keys, certain theoretical frameworks propose operations on encrypted data without disclosing the actual key used. While this does challenge the traditional understanding of keys, it has yet to fully circumvent the requirement for key management and operational complexity.
Another avenue worth exploring is the concept of keyless cryptography, a theoretical model where security mechanisms are not dependent on keys. One such variant is secret sharing, where a plaintext is disseminated amongst multiple parties, each holding a fragment of the original content. No single party possesses enough information to reconstruct the original message alone. However, this approach shifts the concern from keys to the handling of shared secrets, where trust and integrity still play critical roles.
The intriguing idea of threshold encryption further underscores this paradigm. In threshold encryption, a defined number of participants is required to reconstruct a key or secret. While there is a semblance of keyless operation, the underlying structure still mandates the existence of shared keys among participants. By employing advanced mathematical principles and protocols, this method optimizes security while distributing trust, yet the essence of key management remains intricately woven into its framework.
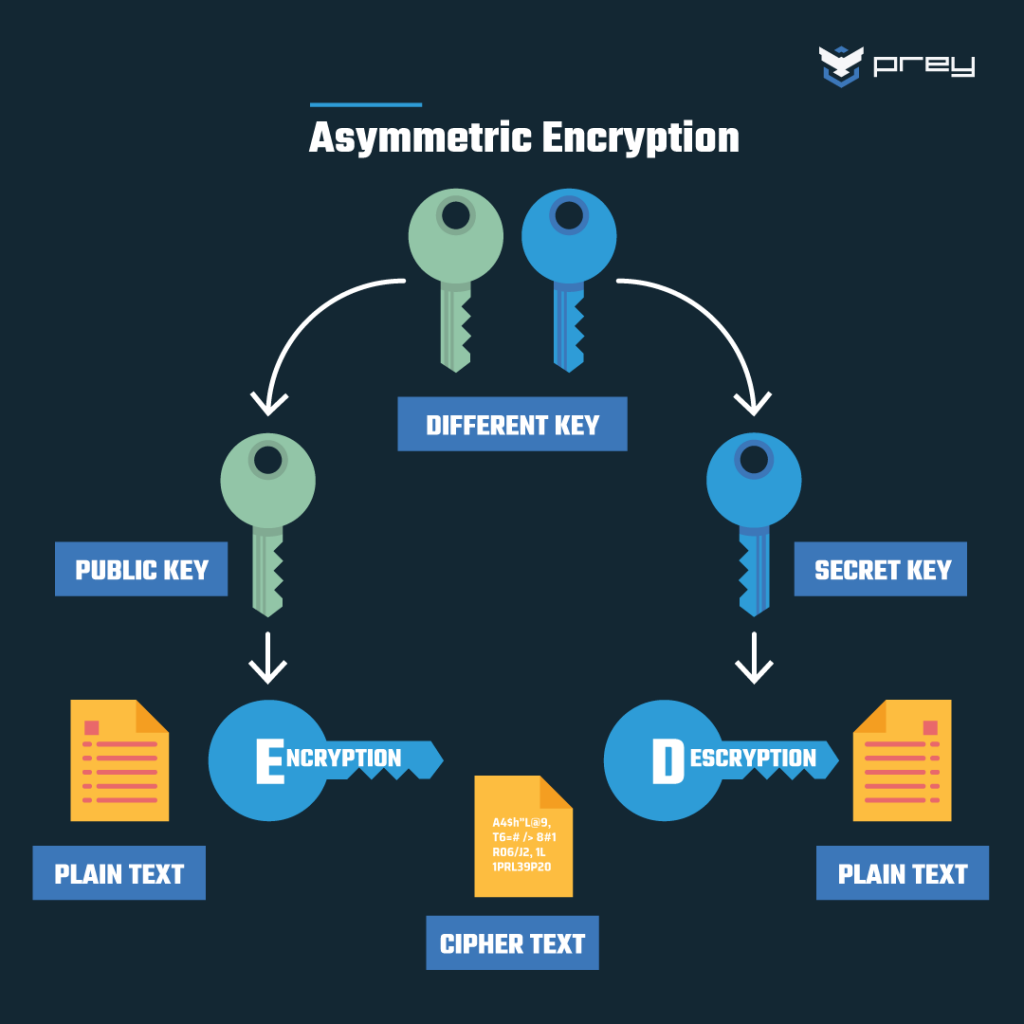
Moreover, one cannot ignore the implications of using public-key infrastructures (PKI). In a PKI system, one party holds a private key while others may access the associated public key. Though it may nudge us towards a keyless illusion, the public-key holds critical importance for the initiation and validation of the encryption process. Cryptographic algorithms such as RSA or ECC harness the powers of complex mathematical relationships, enabling secure communication even in open networks. However, every communication inherently rests on keys, even if masked by public-key architecture.
Diving into more experimental domains, we encounter quantum cryptography. Notably, quantum key distribution (QKD) posits theoretically secure communication channels by utilizing the principles of quantum mechanics. Though QKD itself does employ keys for the purpose of communication, it uniquely offers the potential for security that could redefine the landscape of encryption. The quantum realm poses questions about how traditional cryptographic assumptions will stand in the face of quantum capabilities, leading to ongoing discussions about future encryption paradigms.
Still, it is imperative to address the limitations inherent in redirecting focus away from keys. Key management is fundamental in the cryptographic ecosystem; without appropriate key distribution and storage mechanisms, any advances in encryption methodologies risk subsequent vulnerabilities. The pivotal nature of keys transcends mere convenience; it is integral to building robust security infrastructures that withstand evolving threats. A world devoid of keys would not eliminate risk but merely recontextualize it within a new framework of concerns.
At this juncture, further contemplation is warranted concerning advancements in machine learning and artificial intelligence. Could intelligent systems develop means of data obfuscation that effectively supplant keys? Data may be transformed into adaptive algorithms that obscure content dynamically. While theoretically alluring, the complexity and unpredictability of such methods put them in the paradoxical realm of both innovation and uncertainty. If automation supersedes the static nature of encryption keys, the challenge of assurance emerges; methodologies must be thoroughly evaluated for vulnerability against manipulation or adversarial attacks.
In summary, the concept of encrypting without keys introduces a thought-provoking discourse within the field of cryptography. Despite several theoretical frameworks that suggest alternate methods—such as homomorphic encryption, secret sharing, and quantum cryptography—the reality remains that keys are integral to ensuring data confidentiality and integrity. The exploration of keyless encryption does not serve to miraculously dissolve the necessity of keys, but rather highlights the pressing need for a comprehensive understanding of trust, security, and operational integrity. As technology continues to progress, researchers and practitioners alike must balance ingenuity with responsibility, ensuring that the evolution of cryptographic techniques fortifies rather than undermines the foundational principles of security.







Leave a Comment