Email encryption serves as the metaphorical vault for our digital communications, safeguarding our most sensitive conversations from prying eyes. As our reliance on electronic correspondence burgeons, so too does the imperative to secure these exchanges. However, while email encryption has made significant strides in fortifying data against potential breaches, the question remains: Is it sufficiently impregnable for discussions laden with confidentiality?
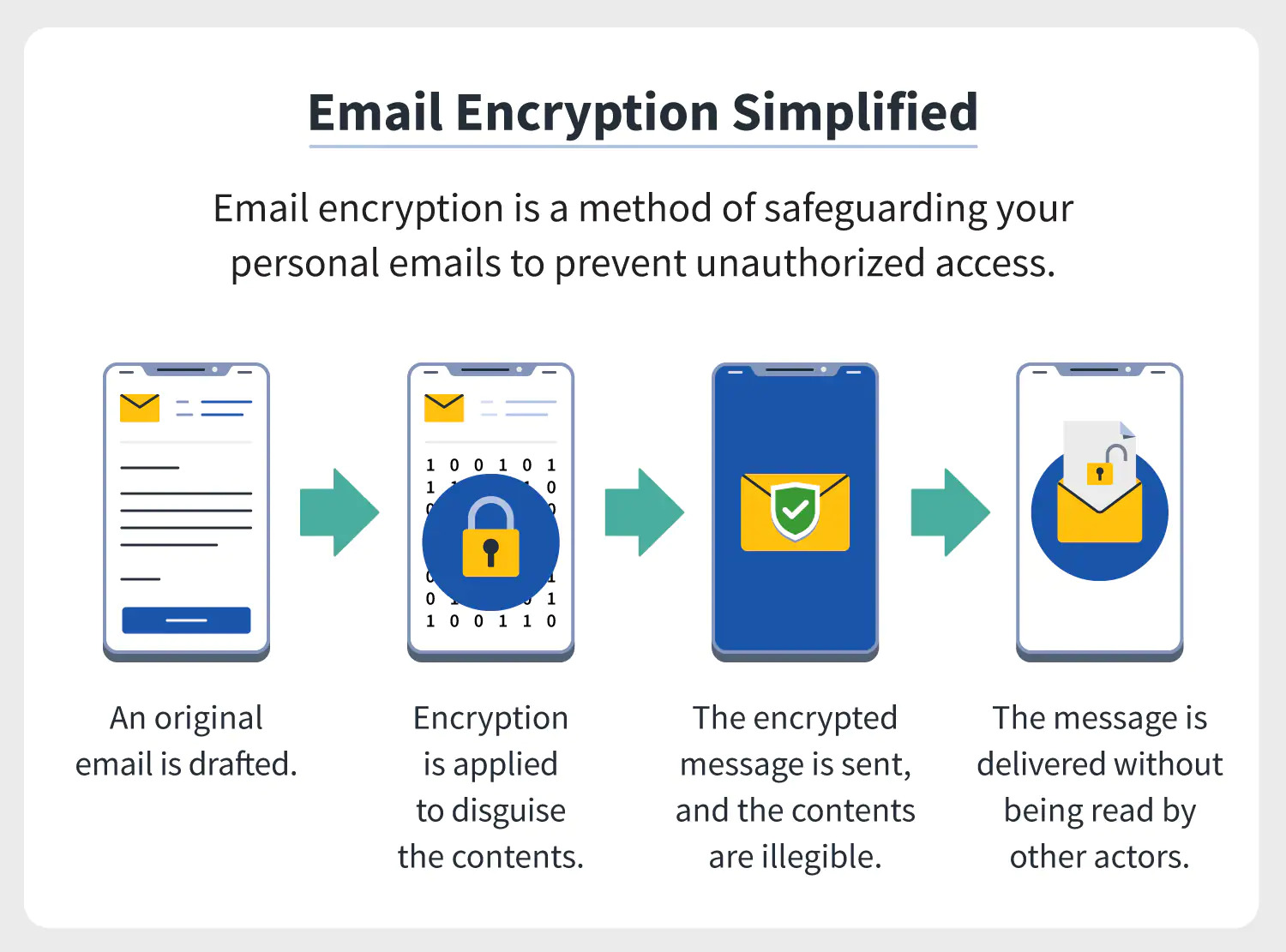
To begin unpacking this question, it is essential to delineate the mechanisms of email encryption. At its core, encryption transmutes plaintext—unprotected information—into ciphertext, a garbled code that remains inscrutable to anyone lacking the requisite decryption key. This intricate dance of cryptographic algorithms underpins two predominant encryption methods: symmetric and asymmetric encryption. Symmetric encryption employs a single key for both encrypting and decrypting a message, akin to a single key that secures a diary, accessible only to its owner. Conversely, asymmetric encryption harnesses a pair of keys—the public and private keys—forming a lock-and-key mechanism that can be likened to fortifying a castle with an indestructible drawbridge, where the public key serves to lock the gate and the private key grants access to those privileged enough to enter.
However, the nuances of email encryption extend far beyond mere technical aspects. There exists a pervasive misconception that once an email is encrypted, it is immune to interception. This is an idealistic fallacy. While encryption significantly mitigates the risk of unauthorized access during transit, vulnerabilities abound. Man-in-the-middle attacks, for instance, can occur when malicious actors exploit weaknesses in the encryption protocol, intercepting and deciphering communications before they reach the intended recipient. Just as one would not trust a delivery person who wanders off the beaten path, it is essential to interrogate the pathways of our digital correspondences.
Furthermore, the email service provider itself may constitute a vulnerability. While user-enforced encryption heralds a new age of privacy, reliance on external platforms means that user data peut be subject to surveillance and data mining practices. In essence, while encryption offers a robust shield, it is futile if the adversaries are already privy to the unlocking mechanisms. Much like a fortress built on hollow ground, the efficacy of encryption falters without an underlying foundation of trust and transparency.
This brings us to the poignant matter of user vigilance. The architecture of encryption can be as robust as the strongest steel, yet its efficacy hinges upon the user’s comprehension and adherence to best practices. Phishing attacks—deceptive attempts to lure users into providing sensitive information—remain a ubiquitous hazard. The human element in the chain of communication is often the weakest link, necessitating continuous education on recognizing these threats. Users must embody the vigilant sentinels of their virtual fortresses, remaining ever-watchful for signs of infiltration.
Moreover, there exist multiple encryption standards, each with its own merits and vulnerabilities. PGP (Pretty Good Privacy) and S/MIME (Secure/Multipurpose Internet Mail Extensions) are two of the most prominent protocols in the email encryption sphere. PGP, with its intricate web of keys and user-defined standards, empowers individuals to control their own security, manifesting a decentralized approach. In contrast, S/MIME streamlines encryption through centralized trust anchors, often appealing to enterprises that require standardized protocols. While both methods proffer security enhancements, the choice between them reflects the user’s unique needs—much like selecting between a tailored suit and a mass-produced garment.
As the landscape of email encryption continues to evolve, so too does the sophistication of cyber threats. Emerging technologies, such as quantum computing, pose an existential challenge to classical encryption algorithms, potentially rendering them obsolete. This inevitability compels a proactive approach to digital security, integrating practices that can withstand the trials of evolving threats. The challenge lies not merely in employing encryption but in adopting a fluid mindset, adapting strategies to outpace the ever-evolving adversarial tactics.
In the pursuit of confidentiality, the interplay between encryption and regulations also warrants exploration. The General Data Protection Regulation (GDPR) and other privacy frameworks advocate for encryption as a requisite standard, positioning it as a legal safeguard against data breaches. This intersection of law and technology underscores the critical importance of encryption in not only securing data but also ensuring compliance with evolving legal landscapes. With the ramifications of a data breach reaching far beyond financial losses, encryption serves as a vital bulwark against reputational harm.
Ultimately, the crux of whether email encryption is safe enough for sensitive conversations hinges upon a confluence of factors: the encryption standard employed, the user’s knowledge, the inclinations of service providers, and the overarching legal framework. As society inches further into a digitally interconnected future, the calculus of privacy demands that individuals and organizations alike adopt a labyrinthine approach, intertwining cutting-edge technology with human vigilance. Just as a ship at sea requires not only a capable captain but also a robust hull to weather the tempests, so too must our email communications be fortified against the omnipresent threats lurking in cyberspace.
Thus, when contemplating the efficacy of email encryption in safeguarding sensitive conversations, let us remain neither overly optimistic nor unduly pessimistic. Rather, it is through a lucid understanding of encryption’s capabilities and limitations that we can navigate the treacherous waters of digital communication with both confidence and caution.







Leave a Comment