The concept of encryption has permeated every segment of our digital lives. Among the myriad algorithms vying for consumer trust and agency, Advanced Encryption Standard (AES) predominantly stands out. Trusted by governments and enterprises alike, AES has risen to prominence as a benchmark for secure data transmission. Yet, despite its extensive adoption, the dialogue surrounding its efficacy raises pertinent questions: Is perfect security indeed attainable, or is it merely an ephemeral ideal—a pipe dream?
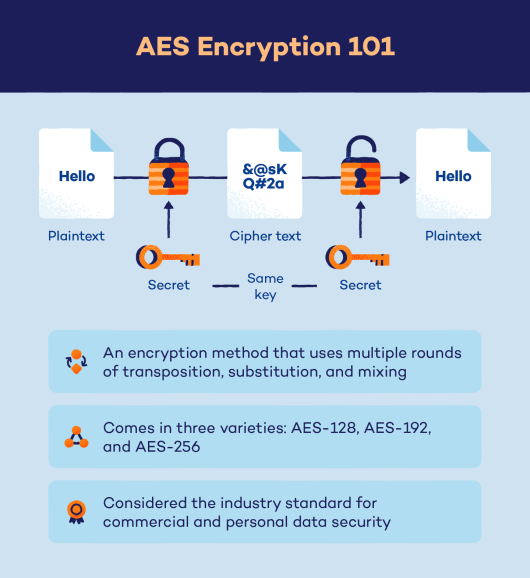
To comprehend the debate surrounding AES, one must first dissect the anatomy of encryption. At its core, encryption is a cryptographic process that transforms plaintext into ciphertext, rendering the original data unintelligible to unauthorized parties. AES, which emerged from the need for a robust encryption standard, employs a symmetric key algorithm with key sizes of 128, 192, or 256 bits. This structural design underpins its resilience against brute-force attacks, where adversaries attempt to decrypt data by exhaustively testing all possible keys. However, beyond mathematical resilience, the conversation surrounding AES is multifaceted, encompassing aspects of practicality, implementation, and evolving threats.
This leads us to contemplate the dual-edged nature of security. While AES boasts significant strengths, the declaration of “perfect security” aligns more closely with a theoretical pursuit rather than an operational reality. The very definition of security is often contextual—what may be deemed secure under one situation can be remarkably vulnerable in another. Cryptography is not merely an algorithmic exercise; it is influenced by human factors, implementation vulnerabilities, and the insatiable adaptability of cyber threats.
Among the most pressing concerns is the potential for key compromise. The strength of AES pivots on the integrity of the secret key. If the key is exposed, all the cryptographic fortifications crumble. A well-implemented AES can be robust, but if users opt for weak passwords or indulge in poor key management practices, the security assurances provided by AES diminish sharply. This raises an intriguing paradox: while AES can theoretically offer near-exceptional security, the human element often introduces weak points that cybercriminals exploit.
Moreover, the emergence of quantum computing casts a long shadow over the future of AES. Quantum algorithms, such as Shor’s algorithm, offer the potential to break cryptographic systems that rely on mathematical difficulty, fundamentally challenging the bedrock of contemporary cryptographic practices. While AES remains secure against these early stages of quantum computing, the cryptographic community is proactively exploring quantum-safe algorithms. As new threats materialize, the need for continuous evolution in encryption standards becomes patently clear. The assertion of “perfect security” must adapt in the face of such disruptive technologies.
As discussions around AES evolve, the integral role of implementation cannot be overstated. In practical settings, AES can be either ineffectively applied or exceptionally executed, translating directly into the robustness of the resulting security. Poor implementations can lead to vulnerabilities such as side-channel attacks, where attackers exploit environmental data surrounding the encryption process—be it timing data or power consumption metrics—to glean critical information. Thus, the true strength of AES often hinges on its deployment rather than the algorithm itself.
Furthermore, legal and ethical dimensions complicate the discourse surrounding encryption. Governments worldwide grapple with the dichotomy between user privacy and national security. In times of crises, the push for backdoors—deliberate vulnerabilities in encryption standards—intensifies. Such measures prompt acrimonious debates about user privacy versus state surveillance. The AES encryption framework, while lauded for its security benefits, becomes a pawn in larger geopolitical games, with its integrity at stake. The dilemma is stark: should personal privacy triumph over collective security, or vice versa?
The landscape surrounding AES is not static; its discourse includes voices from advocates and skeptics alike. Enthusiasts herald AES as a formidable guardian of data integrity. Detractors, meanwhile, cite potential drawbacks—be they compromised key management, implementation flaws, or the shadow of quantum threats—as reasons to doubt its all-encompassing safety claims. The reality lies somewhere in between, revealing a tapestry woven from threads of hope, concern, and continual adaptation.
As the dialogue continues, observers must remain acutely aware that the quest for unassailable security is not merely about selecting the most robust encryption standard; it is a comprehensive endeavor involving a holistic approach toward data protection. AES embodies a critical piece of the puzzle, but it exists within a broader framework of best practices, user awareness, and technological evolution. Addressing the multifaceted challenges posed by cybersecurity necessitates vigilance and preparedness for the unforeseeable developments of the future.
In conclusion, the debate surrounding AES encryption is far from resolved. The question of perfect security remains both tantalizing and elusive. While AES serves as a cornerstone in modern cryptography, its efficacy is intrinsically linked to various factors, including implementation, human behavior, and evolving technological landscapes. As we navigate this labyrinth of uncertainty and complexity, the pursuit of security—perfect or otherwise—will continue to shape the ways in which we protect our digital identities.







Leave a Comment