The advent of public key cryptography has revolutionized the way we secure our digital communications and safeguard sensitive information. At its core, this cryptographic paradigm relies on a pair of keys: a public key, which can be disseminated widely, and a private key, which must remain confidential. This dual-key mechanism grants unprecedented control over data encryption and decryption, raising an essential question: Can a public key decrypt your secrets? To address this query, it is imperative to dissect the intricacies of public key cryptography, its operational mechanisms, and the implications for data security.
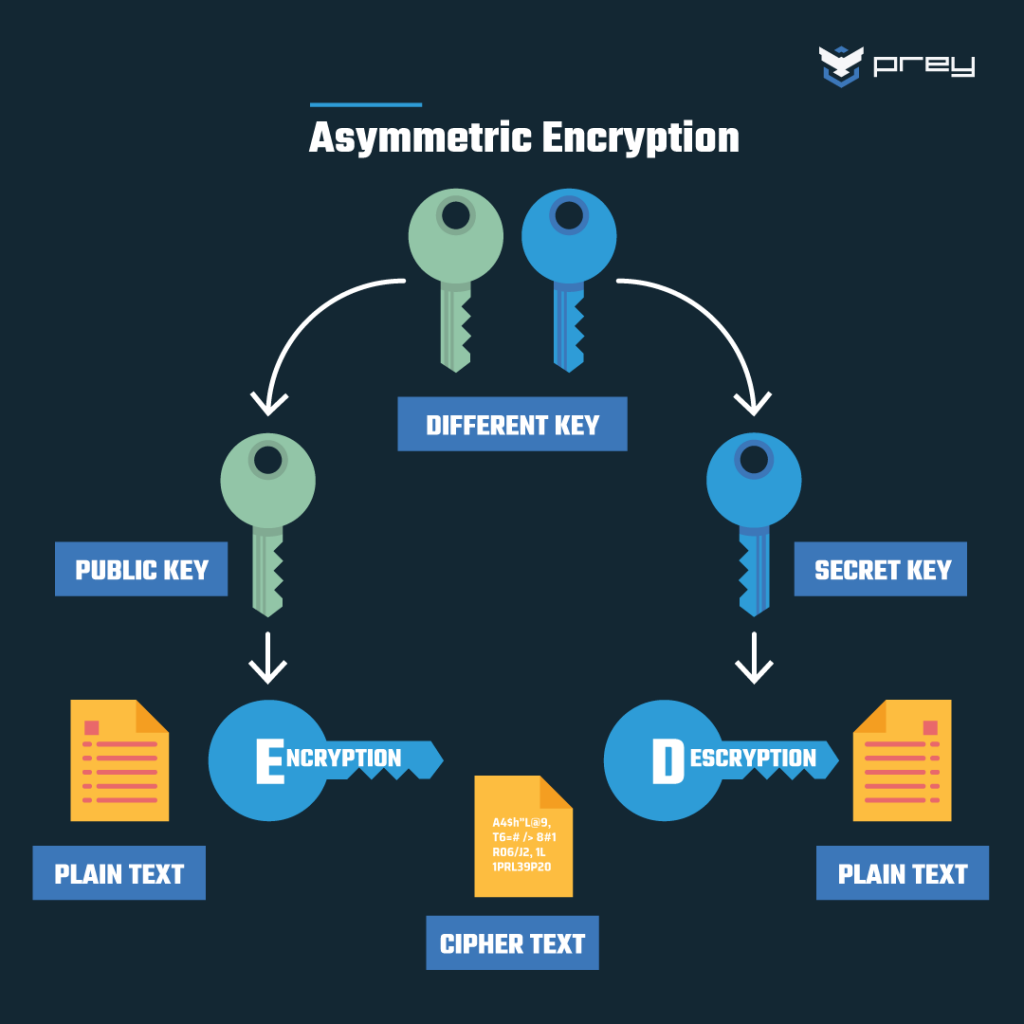
To delve deeper, let us define the fundamental principles underlying public key cryptography. Public key cryptography, also known as asymmetric cryptography, allows users to engage in secure communication without the necessity of sharing a private key beforehand. This system was primarily conceived to facilitate secure transactions over insecure mediums, such as the internet. The primary advantage lies in its ability to enable users to share their public keys freely, engendering a framework where disparate entities can encrypt messages intended for one another, while ensuring that only the intended recipient possesses the requisite private key to unlock the information.
Public key cryptography operates on mathematical algorithms that secure data through complex transformations. Two prominent examples of public key algorithms are RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography). Both of these systems generate keys based on algorithmic constructs that are computationally intensive, thus fortifying the security landscape. The workings of RSA hinge on the difficulty of factoring large composite numbers, whereas ECC capitalizes on the algebraic structure of elliptic curves over finite fields. This disparity in their operational frameworks introduces varied levels of efficiency and security, underscoring the engineering marvels underpinning modern cryptographic systems.
Now, to approach the crux of the question: Can a public key decrypt your secrets? The straightforward answer is no; a public key cannot decrypt information that it encodes. Instead, it is merely a conduit for encryption. When a sender employs the recipient’s public key to encrypt a message, that encrypted data can only be decrypted using the corresponding private key. This specific asymmetry lies at the heart of the security promise of public key cryptography. It ensures that even if a third party intercepts the encrypted message, deciphering that information remains computationally unfeasible without access to the private key.
To elucidate this process, consider an example involving Alice and Bob. Alice possesses Bob’s public key, which she uses to encrypt a message conveying sensitive information. In this transaction, the confidentiality of the message is preserved because only Bob retains the exclusive means to decrypt it with his private key. Therefore, even if an adversary were to acquire the encrypted data, without the private key, they remain powerless to retrieve the original message. This encapsulation of security reinforces trust within digital communications, making public key cryptography indispensable in online transactions, secure email exchange, and various applications requiring confidentiality.
Nevertheless, the supremacy of public key cryptography is not without its vulnerabilities. The paradox of cryptography lies in the fact that while it offers a robust shield against unauthorized access, it is not immune to threats. The realm of public key cryptography experiences potential breaches primarily through inadequate private key management practices or exploitation of vulnerabilities inherent in the cryptographic algorithms themselves. A compromised private key, for instance, will grant any malicious entity the ability to decrypt information that was ostensibly secure. Additionally, the emergence of quantum computing poses a prospective quantum threat, as it could dismantle the security fabric of current public key systems, emphasizing the need for future-proof cryptographic solutions.
Moreover, the philosophical implications of public key cryptography extend into the dimensions of privacy and computational ethics. As society grapples with the increasing interconnectivity fostered by digital advancements, the safeguarding of one’s secrets transcends mere technical endeavors, evolving into a moral imperative. Public key cryptography empowers individuals by bestowing control over their personal information, reinforcing the sanctity of privacy. This delicate balance between security and accessibility obliges us to remain vigilant in adopting best practices, aiming to mitigate risks while capitalizing on the myriad benefits offered by this cryptographic system.
In conclusion, the inquiry surrounding the capability of a public key to decrypt secrets elucidates the underlying mechanics of public key cryptography—an arena characterized by both promise and peril. Public key encryption remains a formidable tool for securing digital communications, assuring that secrets remain veiled from prying eyes, albeit contingent on the integrity of private key management. The cyclical nature of innovation and threat mandates an ongoing commitment to bolster cryptographic protocols, embracing an adaptive mindset as technology evolves. As we navigate the complexities of the digital age, the juxtaposition of convenience and security persists, ultimately guiding our ethos in the pursuit of a secure and private online existence.







Leave a Comment